Warning! The content within this article is over 36 months old and, therefore, may be out of date.
HOWTO: Replace a VMCA certificate via the GUI in vSphere 6.5 with PSC & VCSA
Platform Services Controller vCenter VCSA VMCA VMware vSphere
Published on 25 March 2017 by Christopher Lewis. Words: 344. Reading Time: 2 mins.
Introduction
In this blog post we will walkthrough how to use the GUI to replace the SSL certificates on both the vCenter Server Appliance (VCSA) and Platform Service Controller (PSC) in vSphere 6.5.
Step by Step Guide
Prerequisites
- A VMCA SSL Certificate (such as
root_signing_cert.cer) - A RSA Private Key (such as
root_signing_cert.key)
Process Overview
The high level steps are as followed:
- Log into the External Platform Services Controller.
- Replace the Root Certificate.
- Connect to the PSC Appliance.
- Renew the Machine SSL Certificate.
- Renew the Solution User Certificate.
- Connect to the VCSA Appliance.
- Renew the Machine SSL Certificate.
- Renew the Solution User Certificate.
- Reboot the Platform Services Controller.
Process Breakdown
Log into External Platform Services Controller
- Navigate to
https://psc-appliance.fqdn/psc.
- Log in using the SSO Administrator account (e.g.
administrator@vsphere.local) and password.
Renew the Root Certificate
- Click Certificate Authority > Root Certificate.
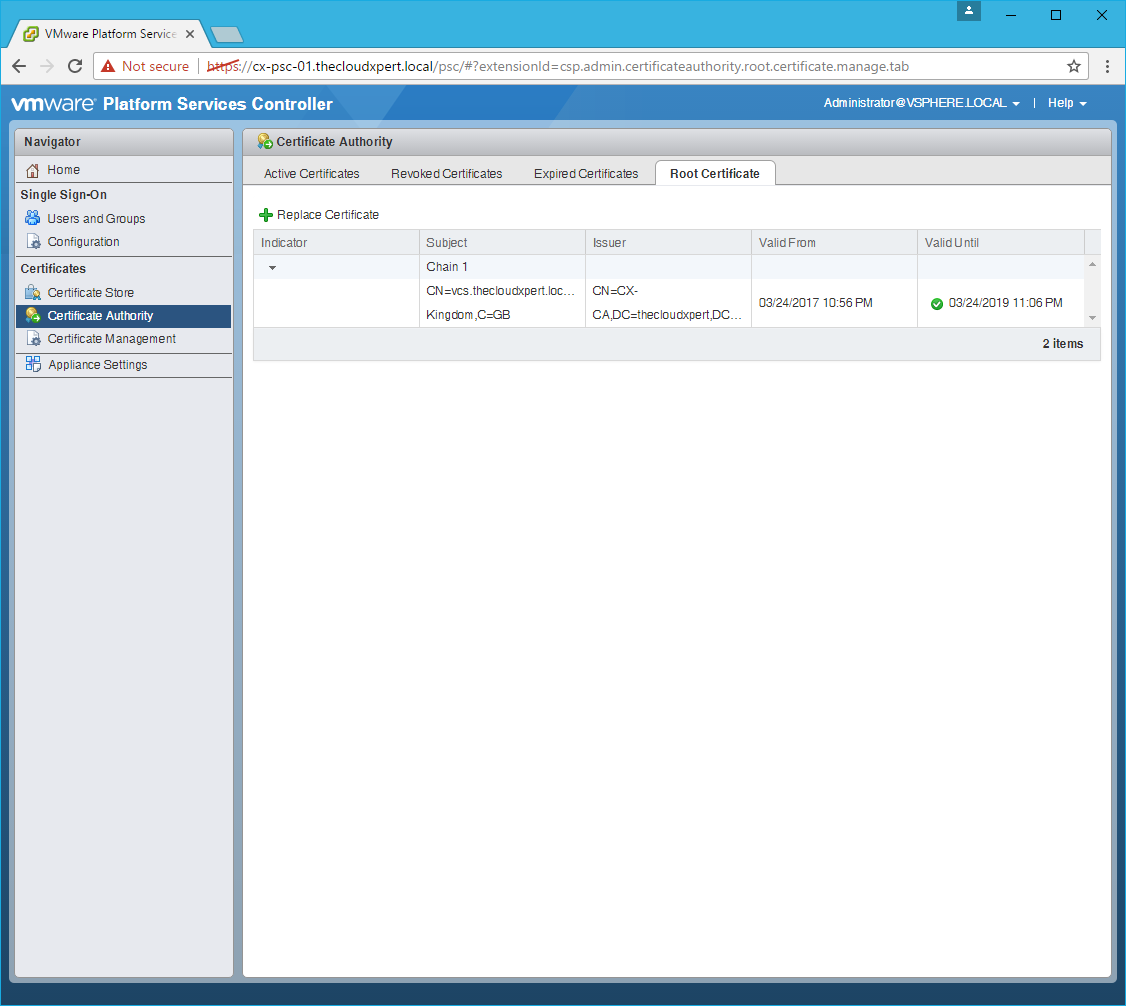
- Click Replace Certificate.
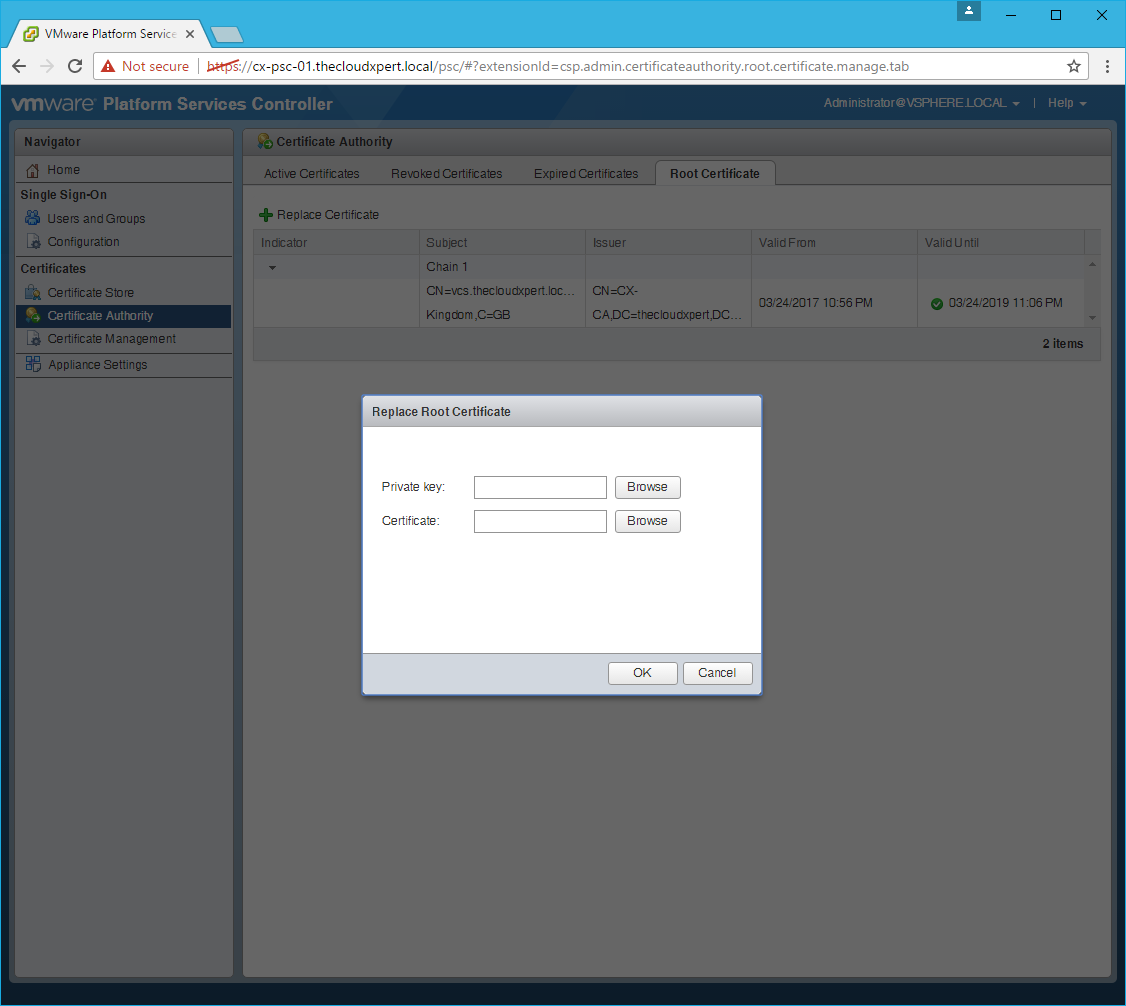
- Click Browse and locate the Private Key file and click Open.
- Click Browse and locate the VMCA Certificate file and click Open.
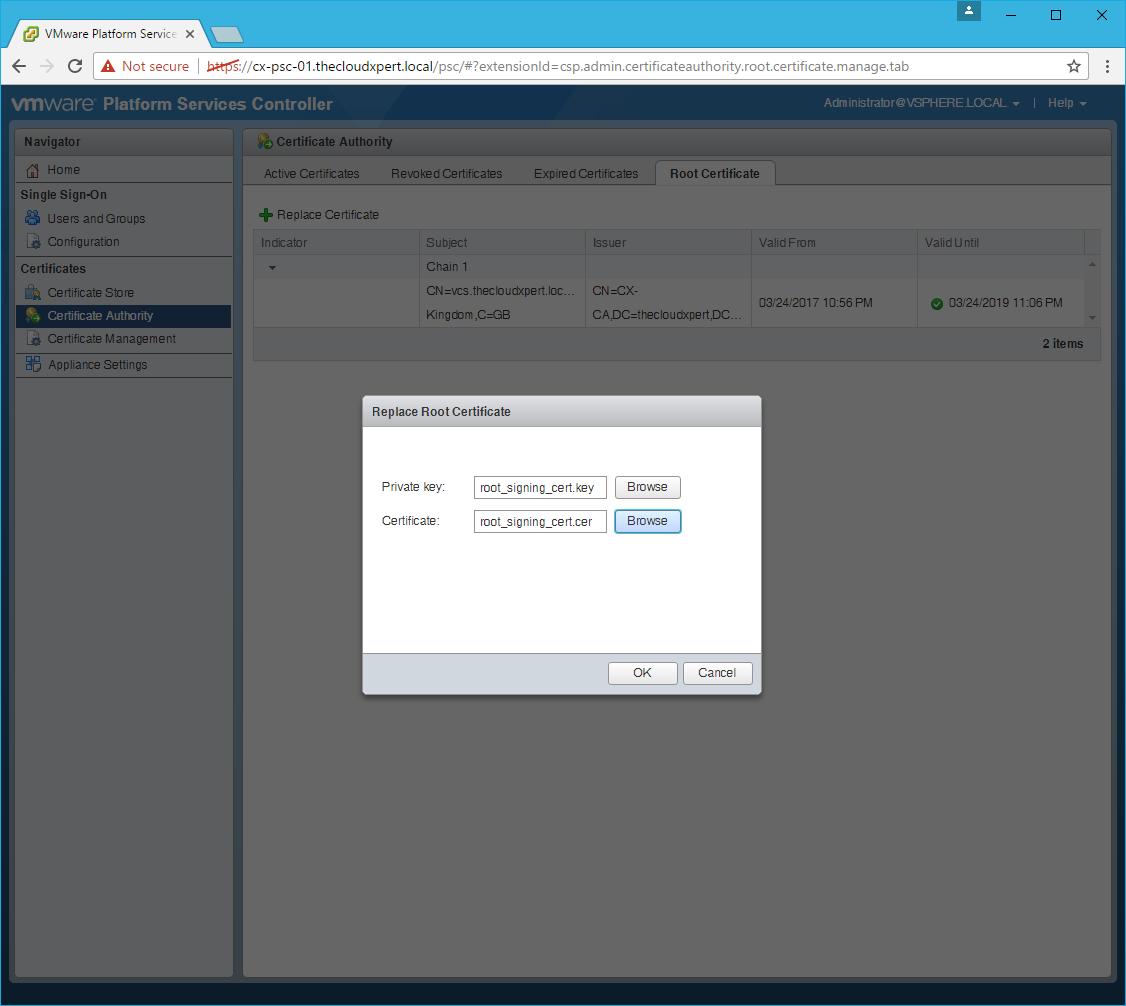
- Click OK.
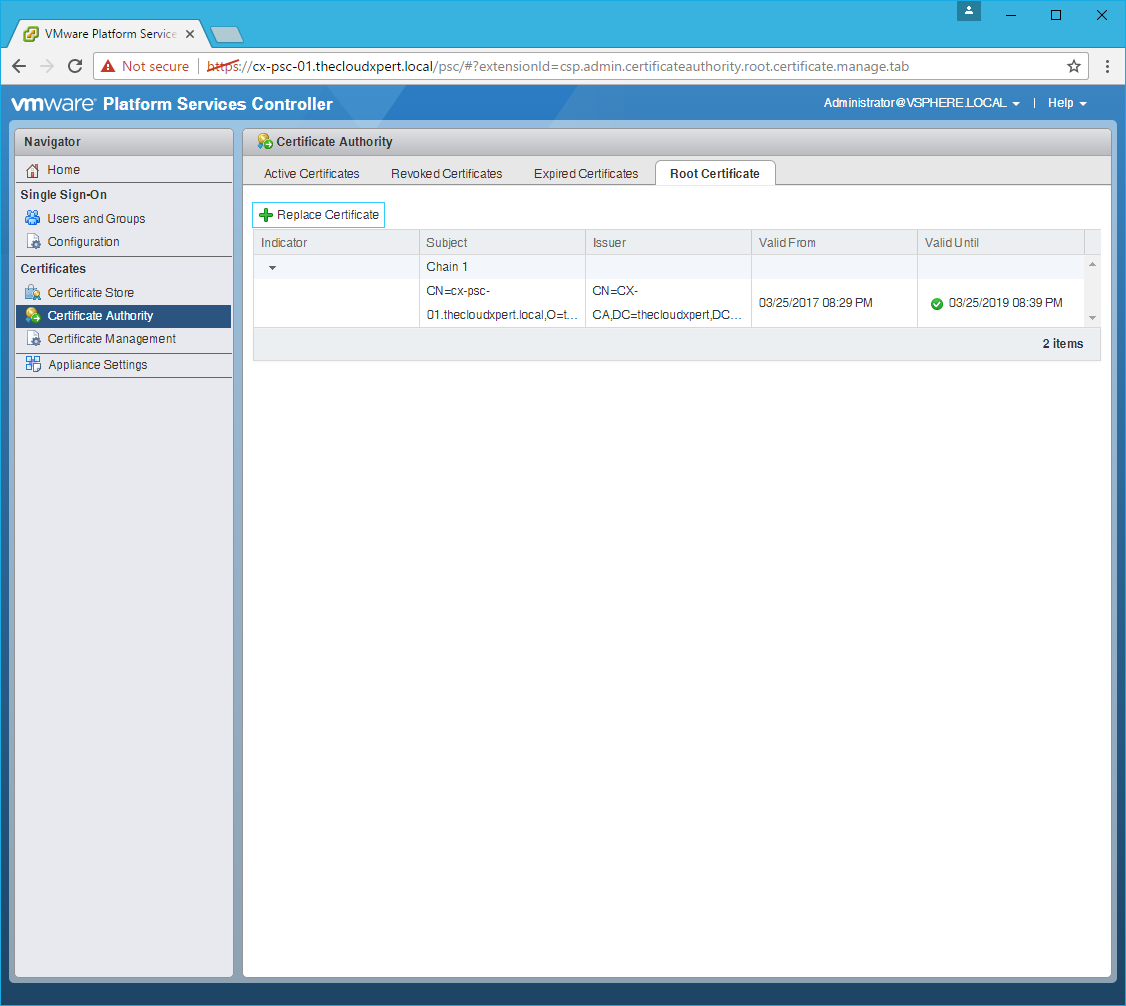
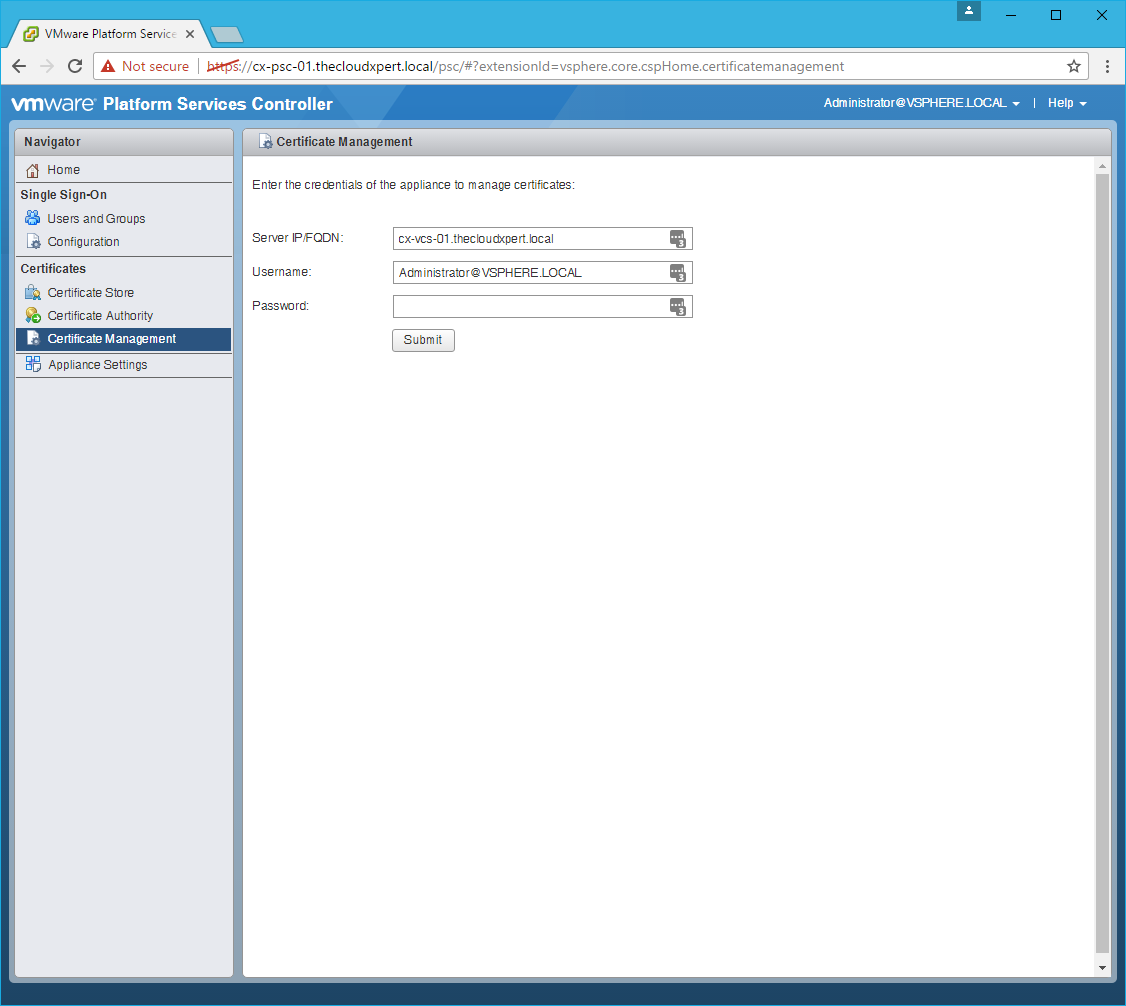
Connect to the Platform Services Controller
- Click Certificate Management.
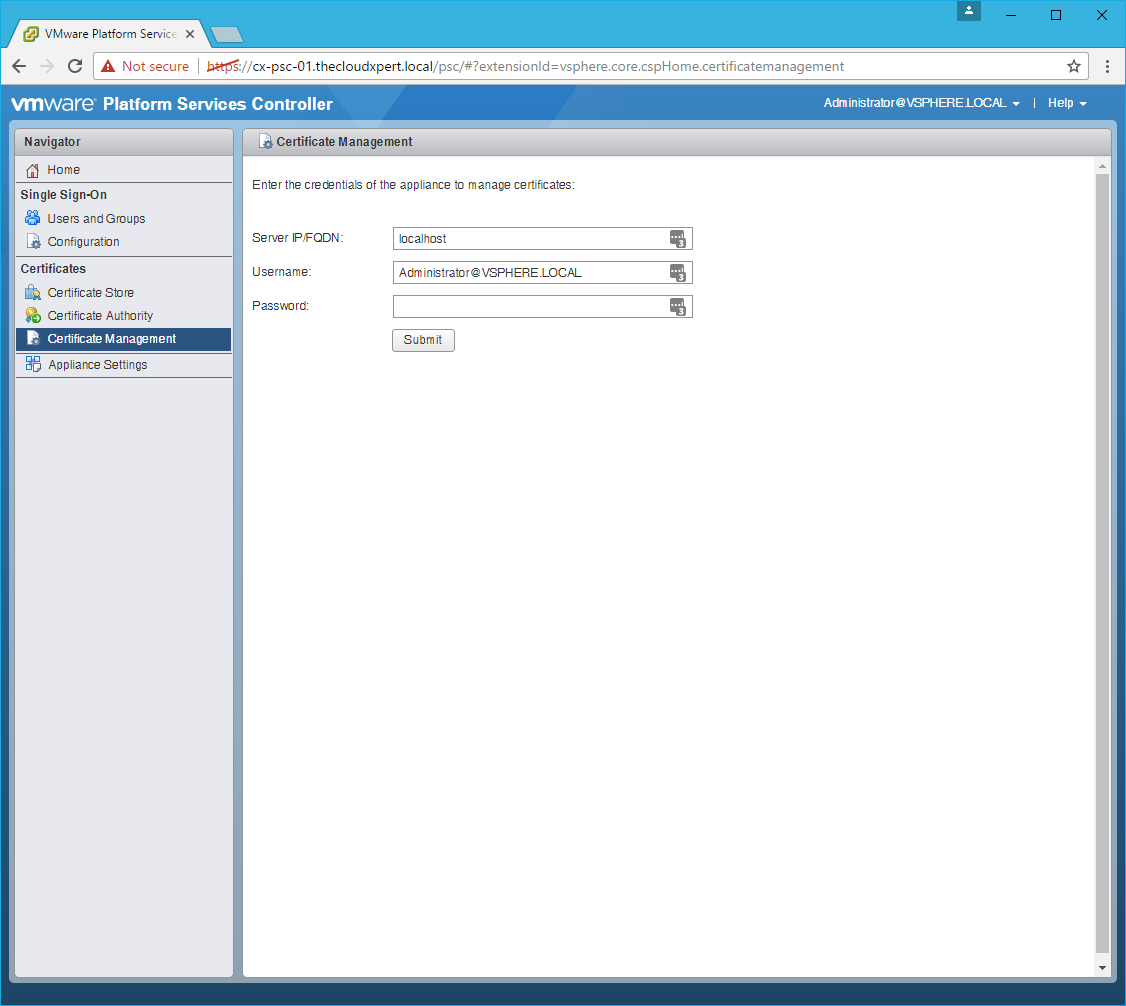
- Type the SSO Administrator password and click Submit.
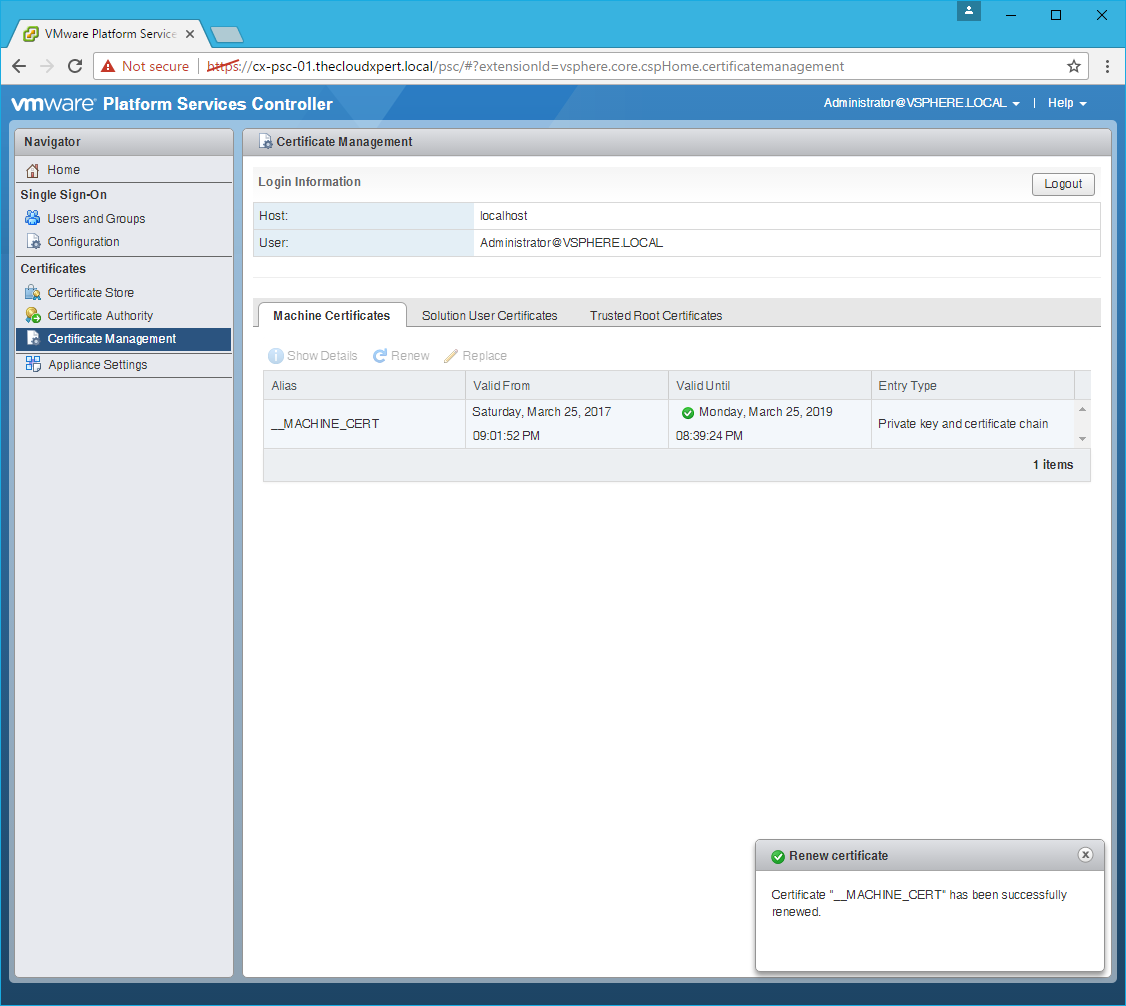
Renew the Machine SSL Certificate
- Click the Machine Certificates tab.
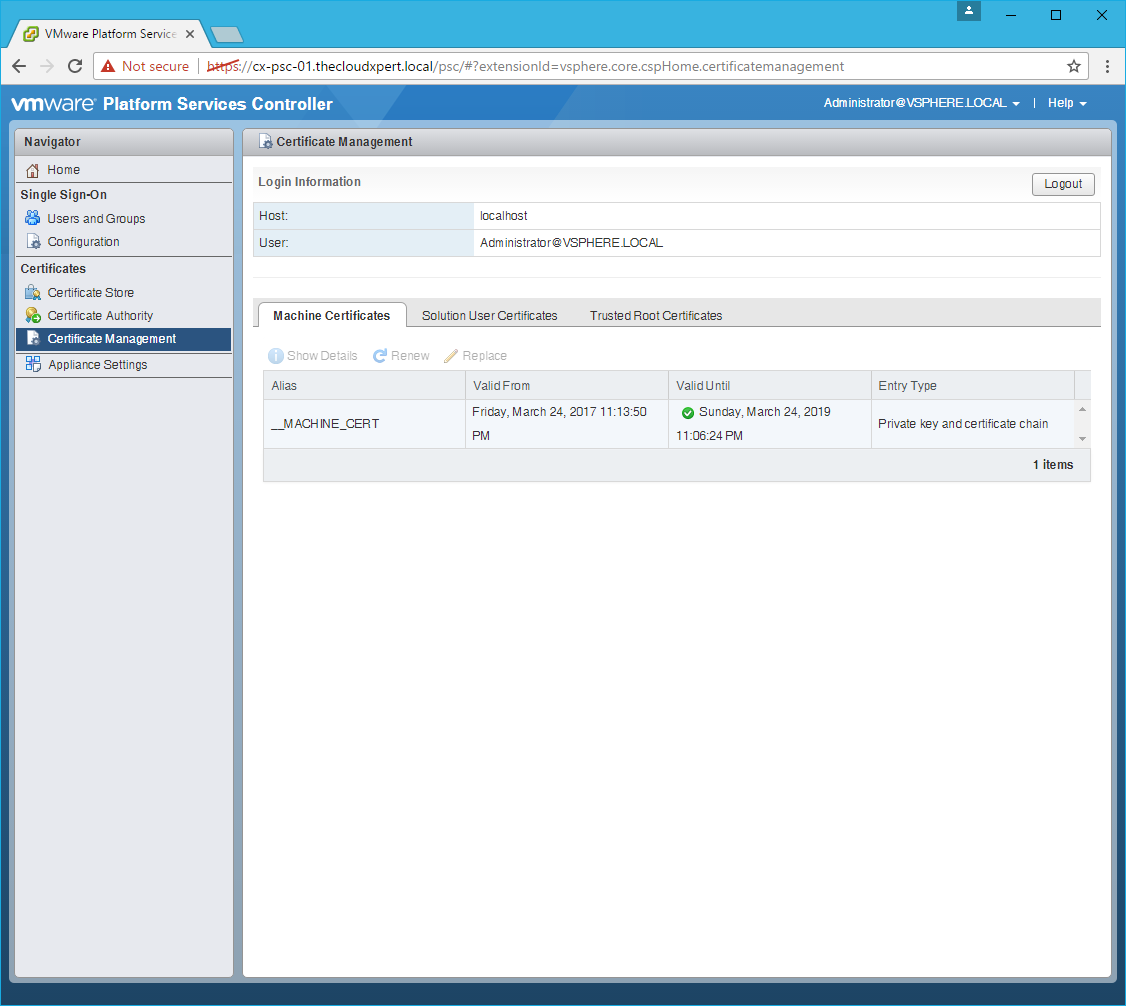
- Select the
__MACHINE_CERTand click Renew.

- Click Yes.
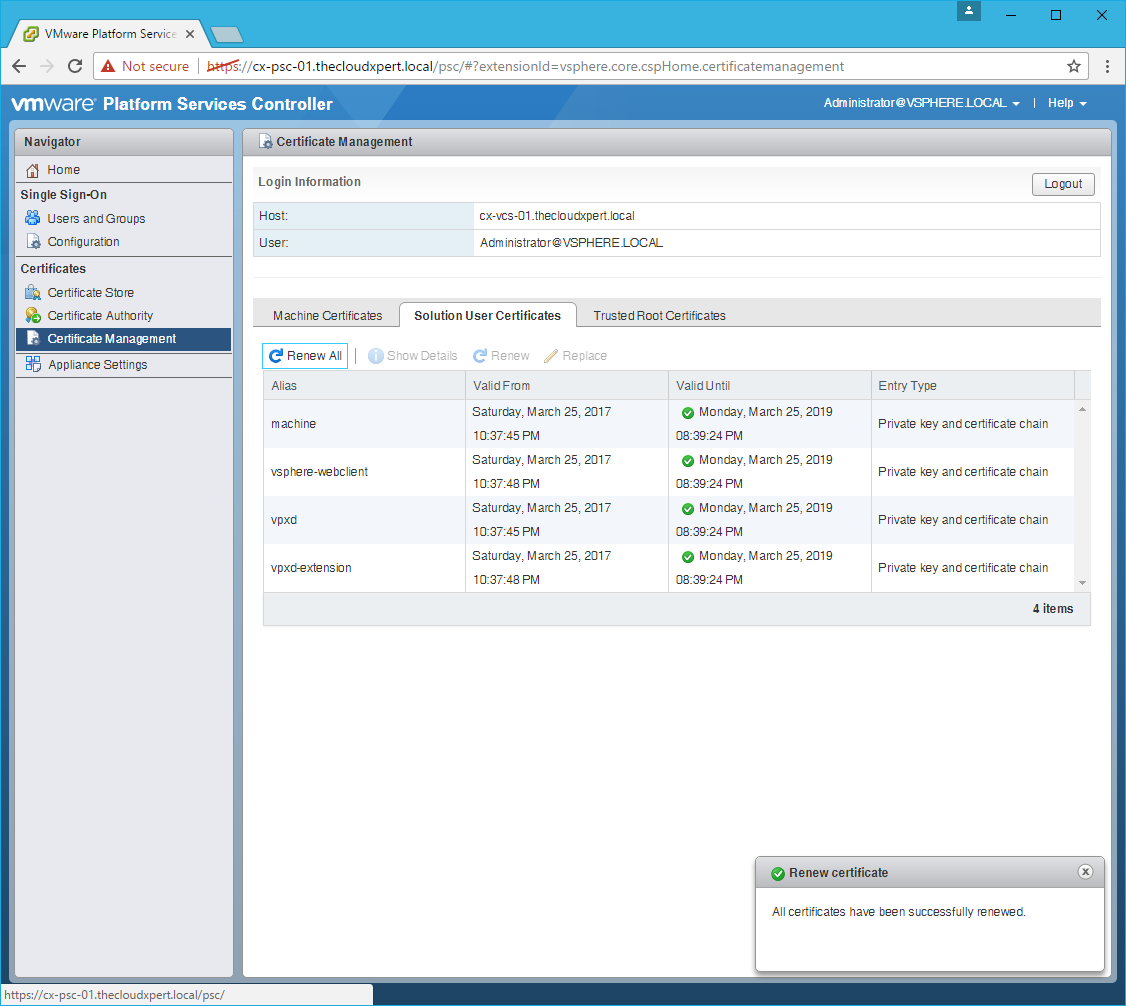
Renew the Solution User Certificates
- Click the Solution User Certificates tab.
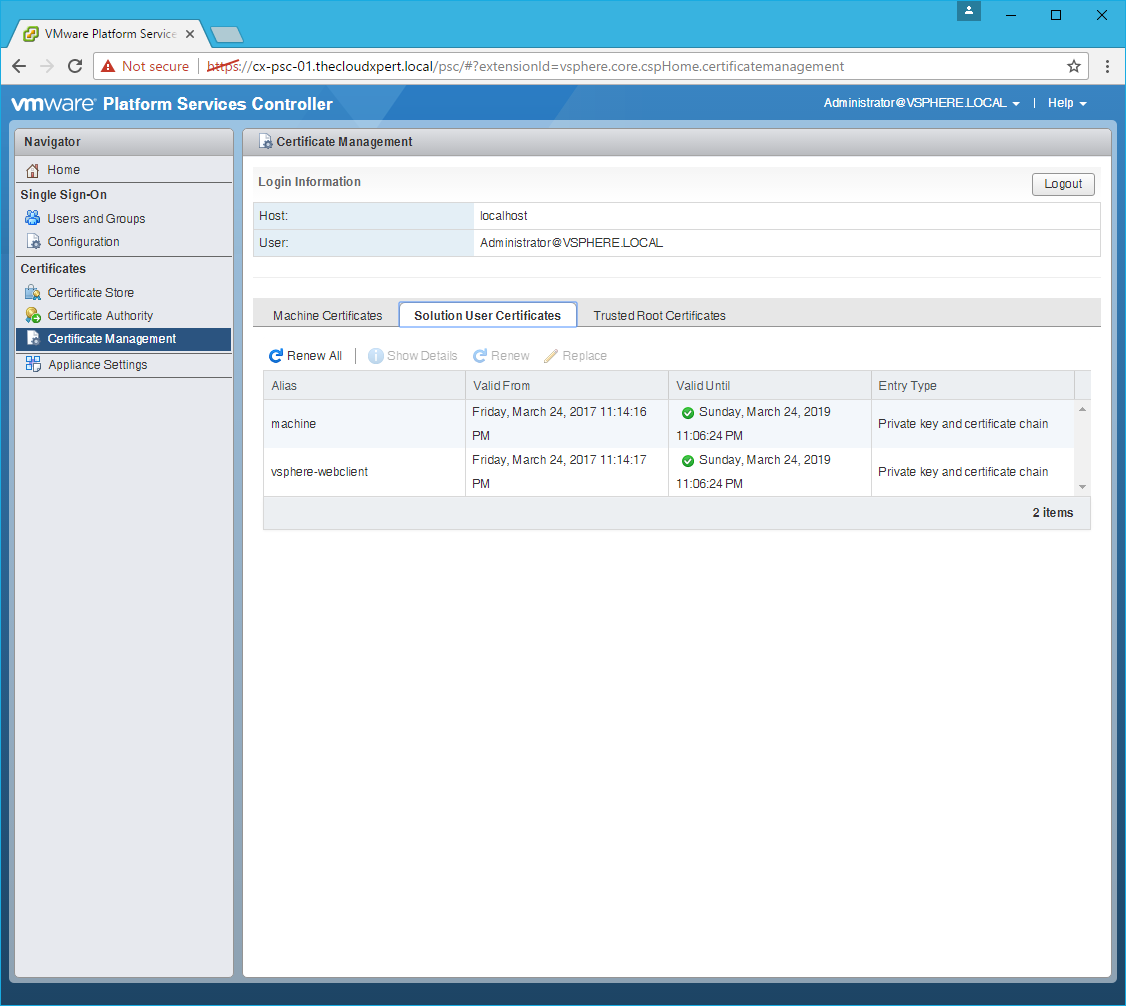
- Click Renew All.
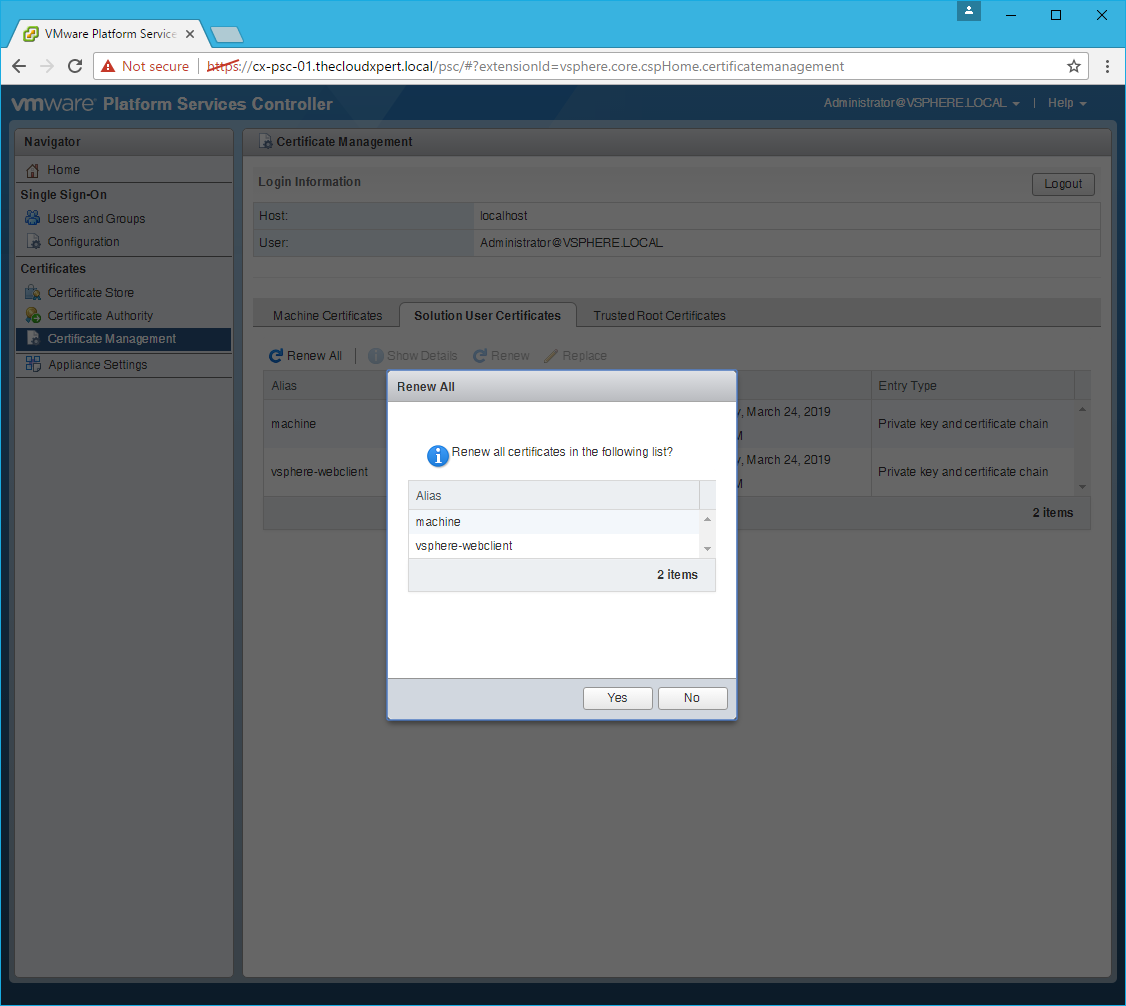
- Click Yes.
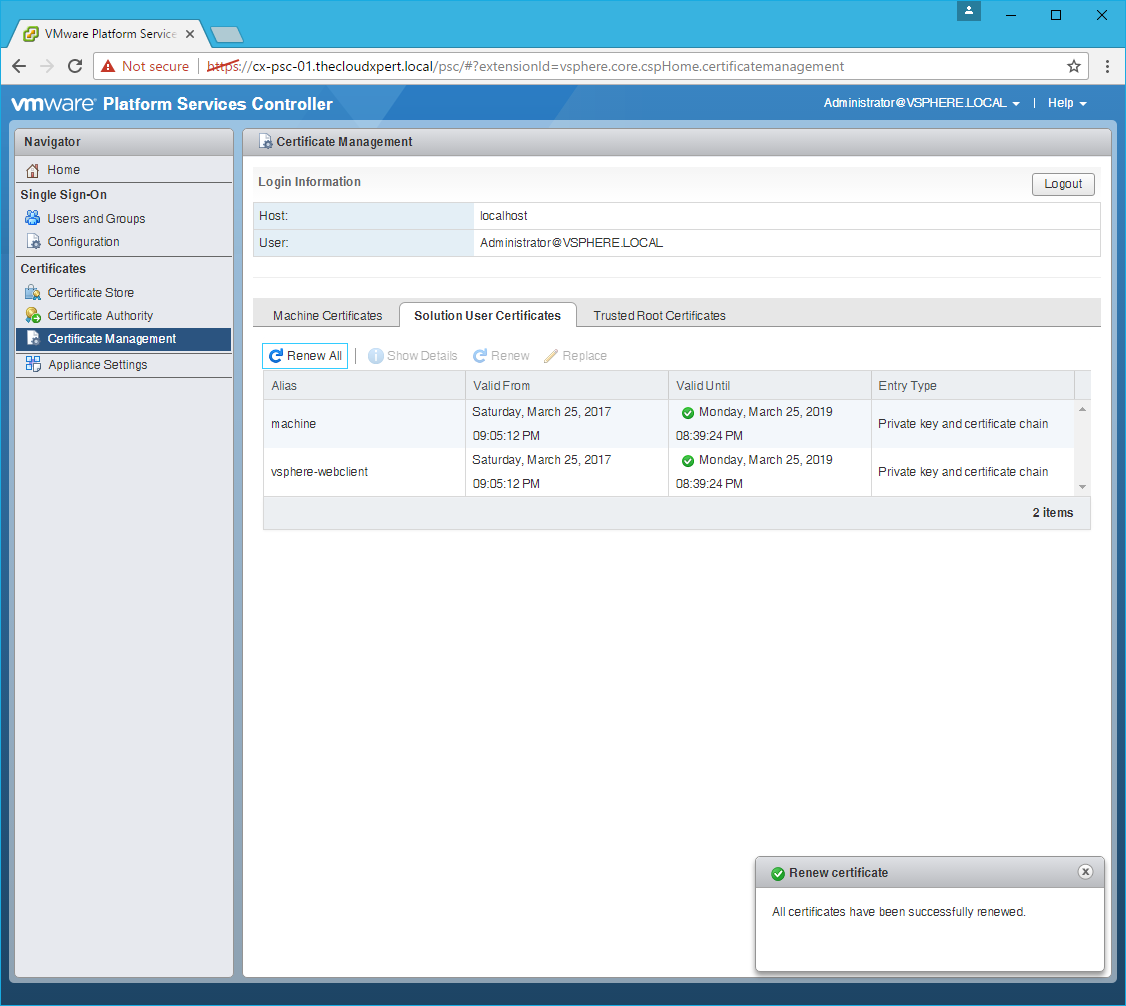
- Click Logout.
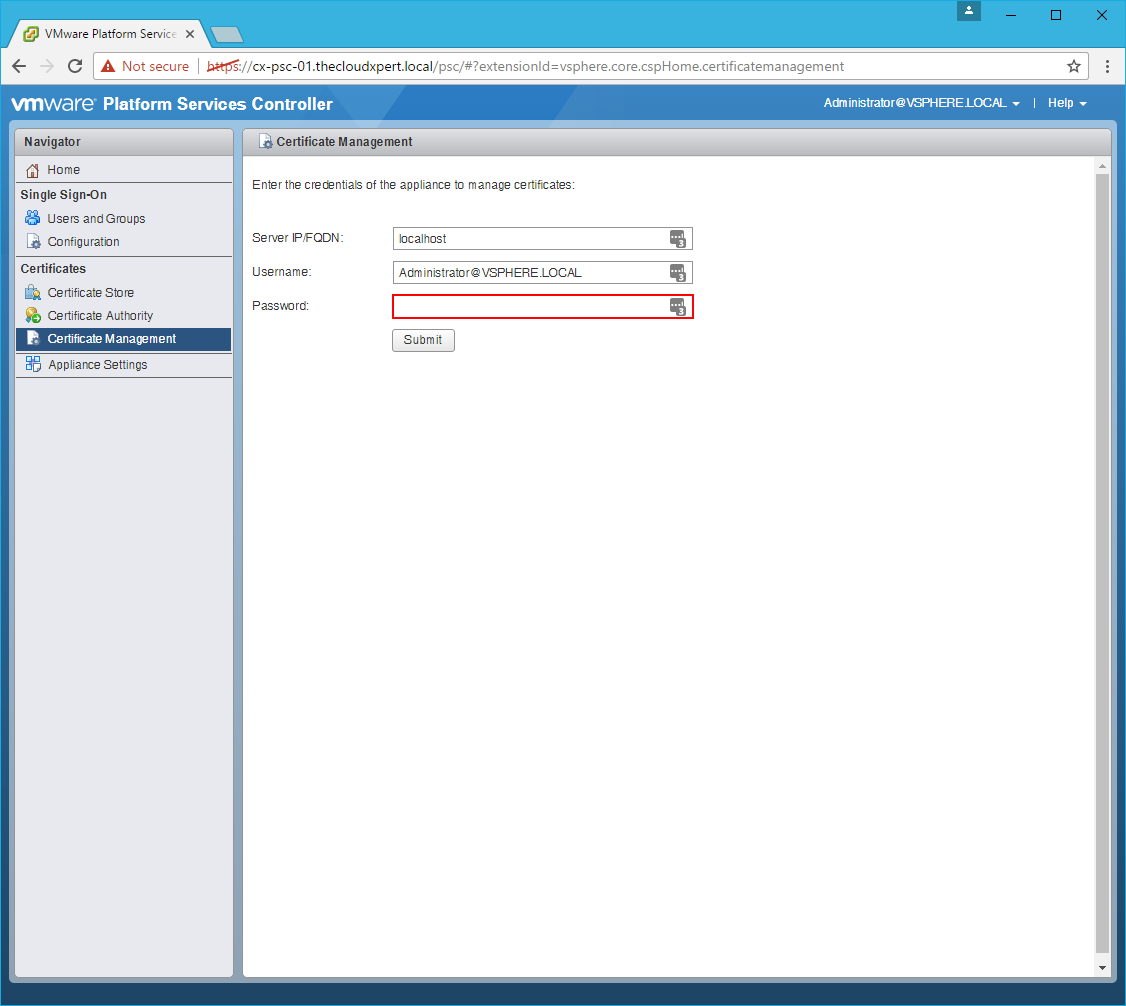
Connect to the vCenter Server
- Type the
vcenter.fqdninto the Server IP/FQDN text box and then enter the password for the SSO Administrator.
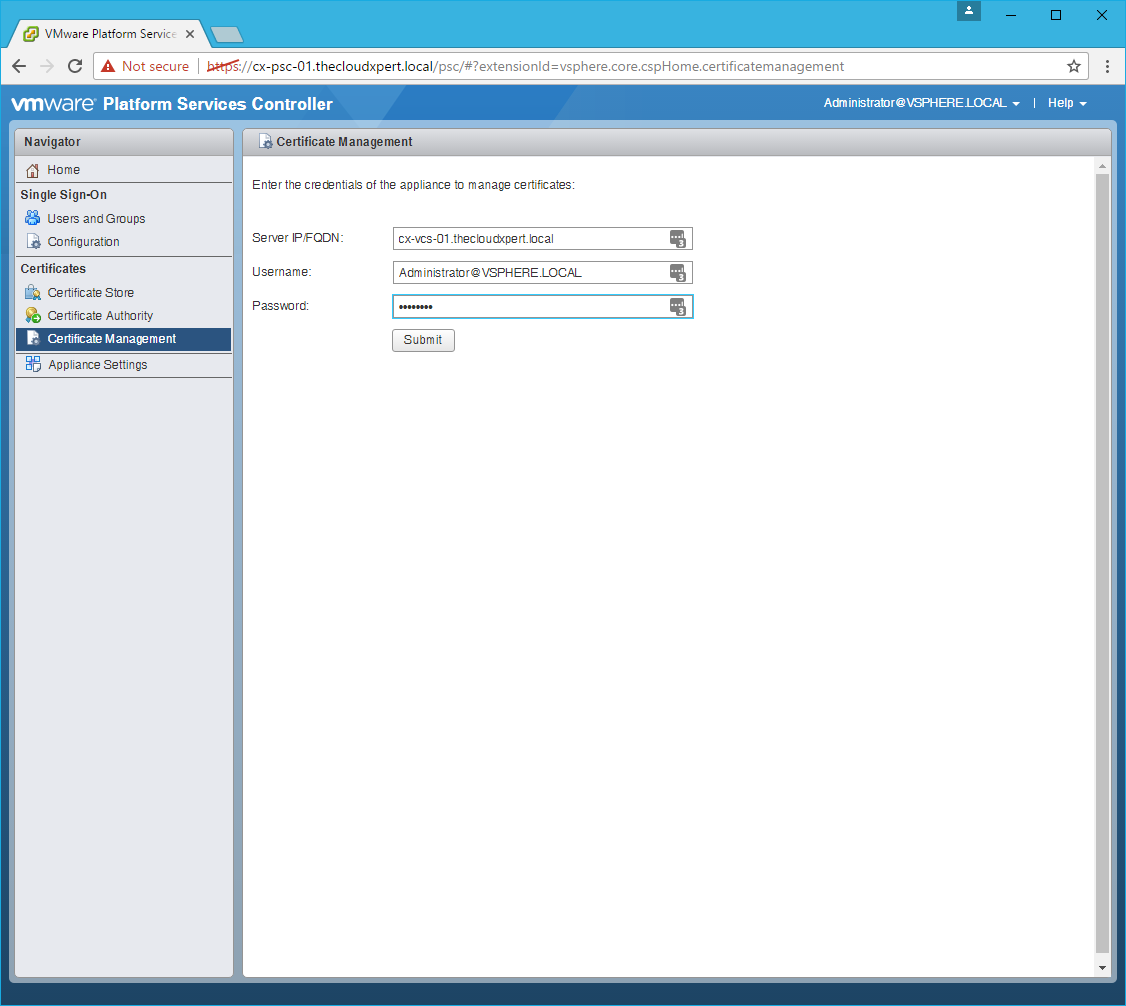
- Click Submit.
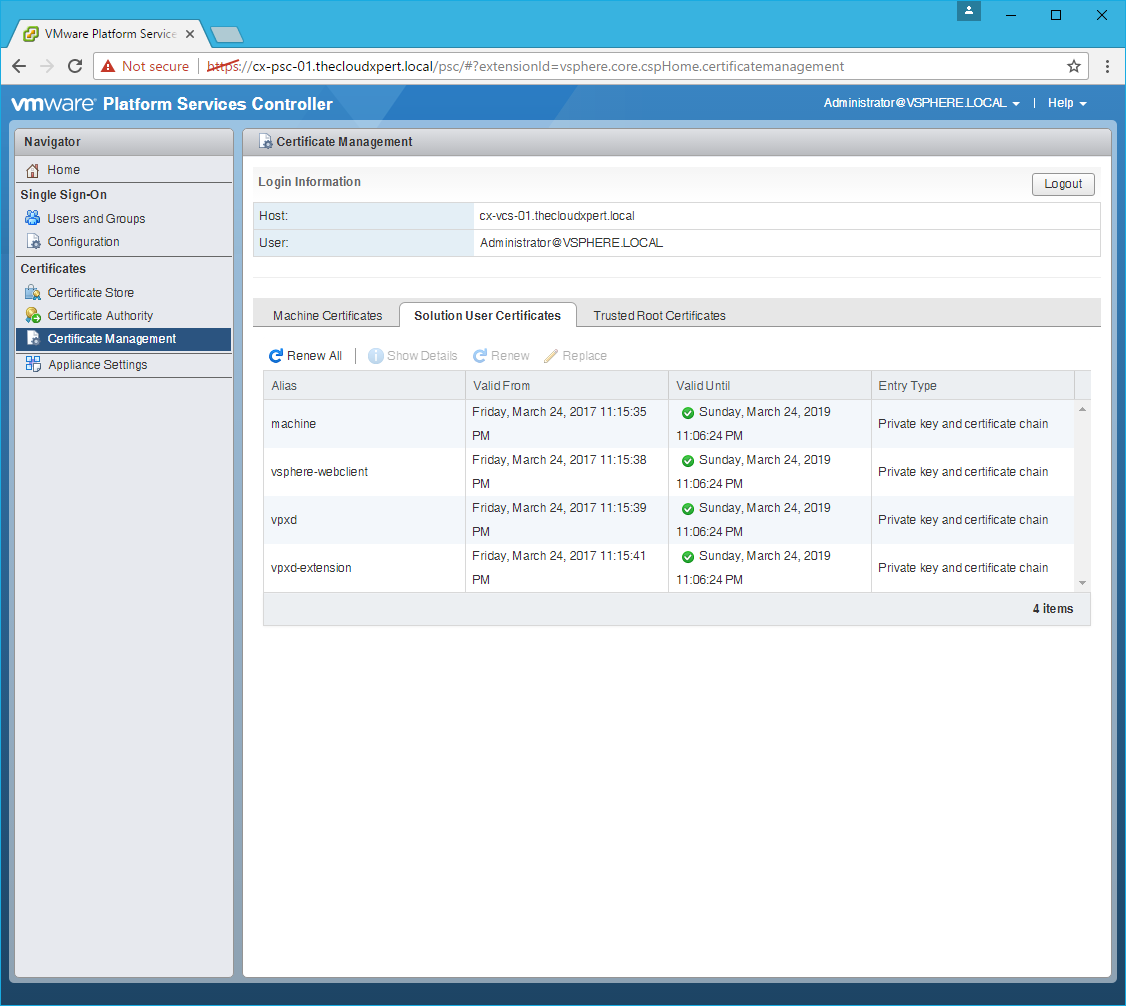
Renew the Machine SSL Certificate
- Click the Machine Certificates tab.
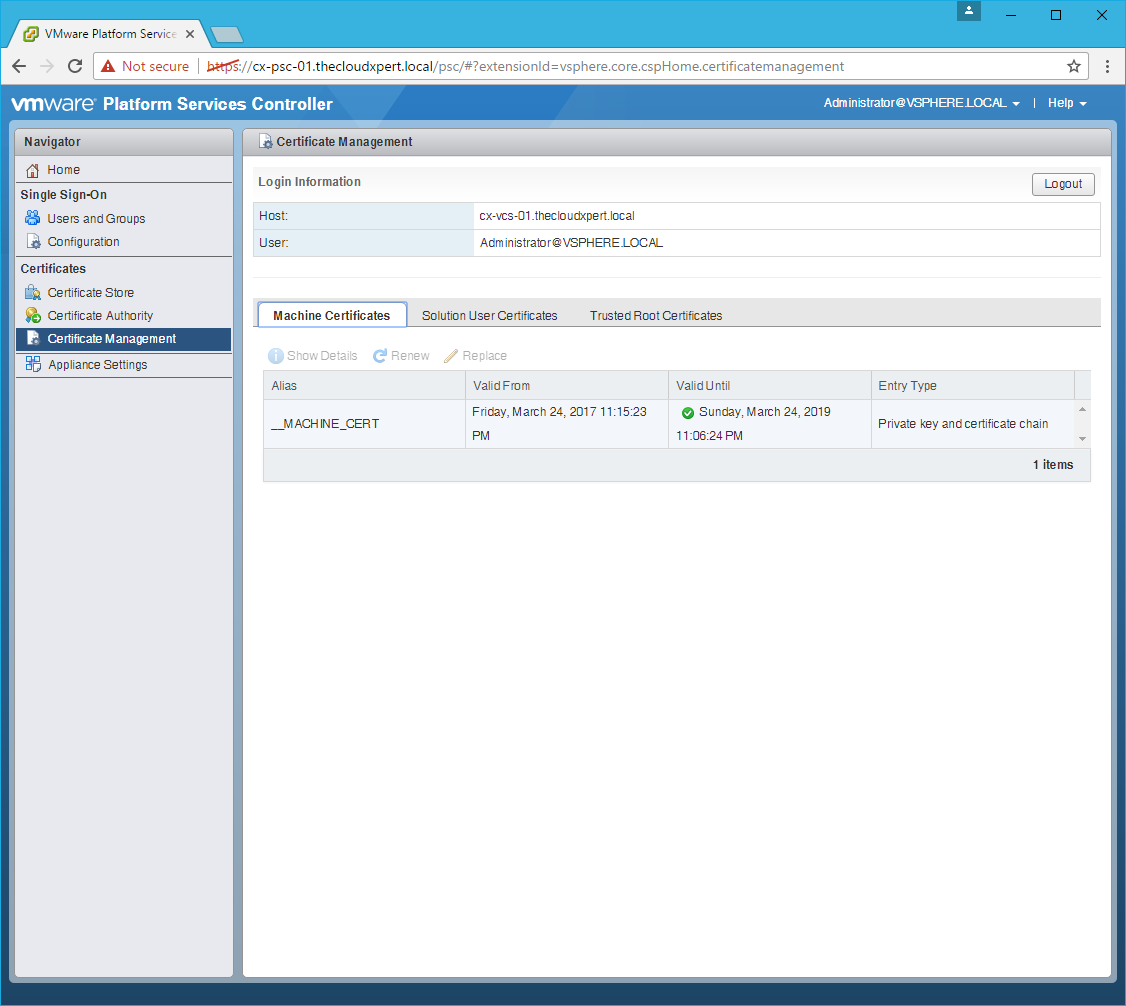
- Select the
__MACHINE_CERTand click Renew.
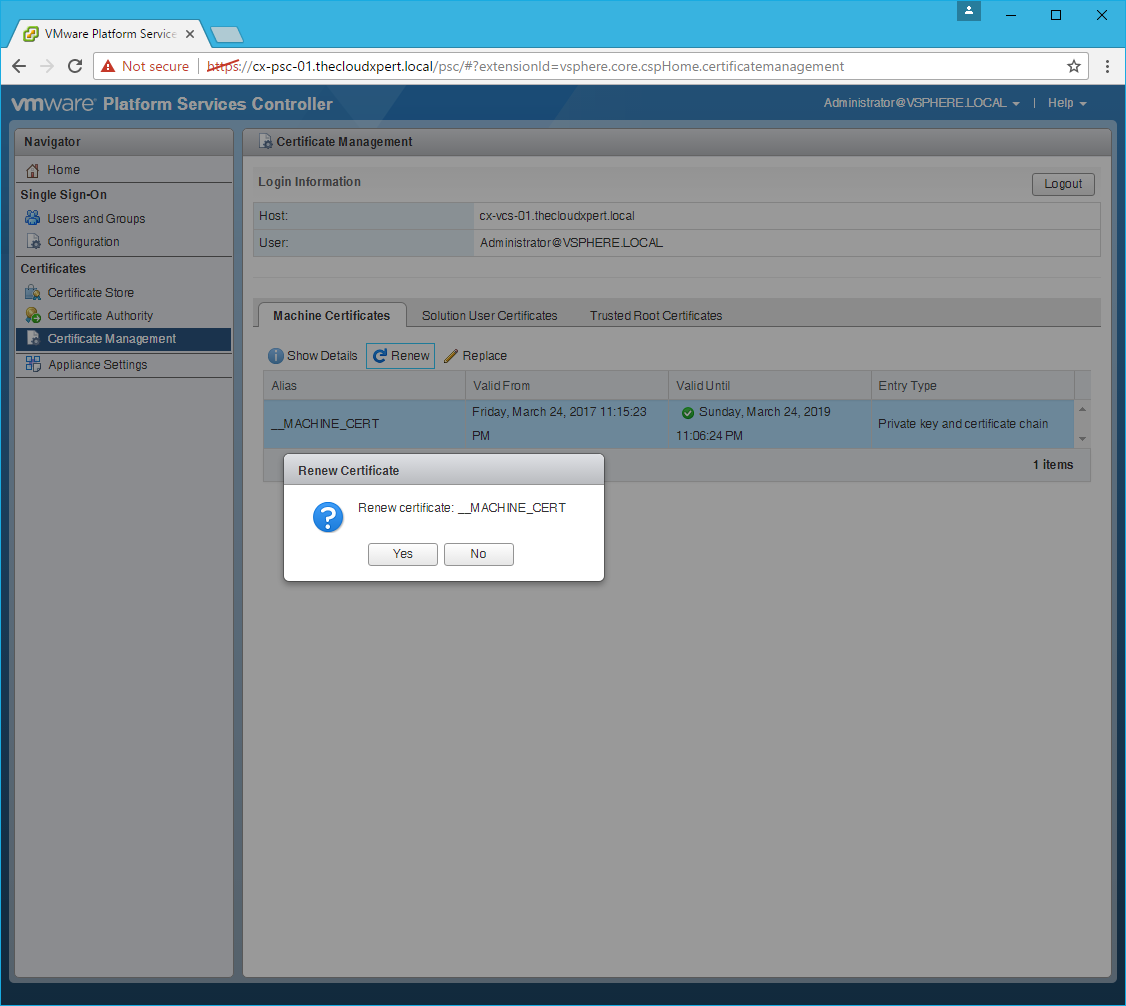
- Click Yes.
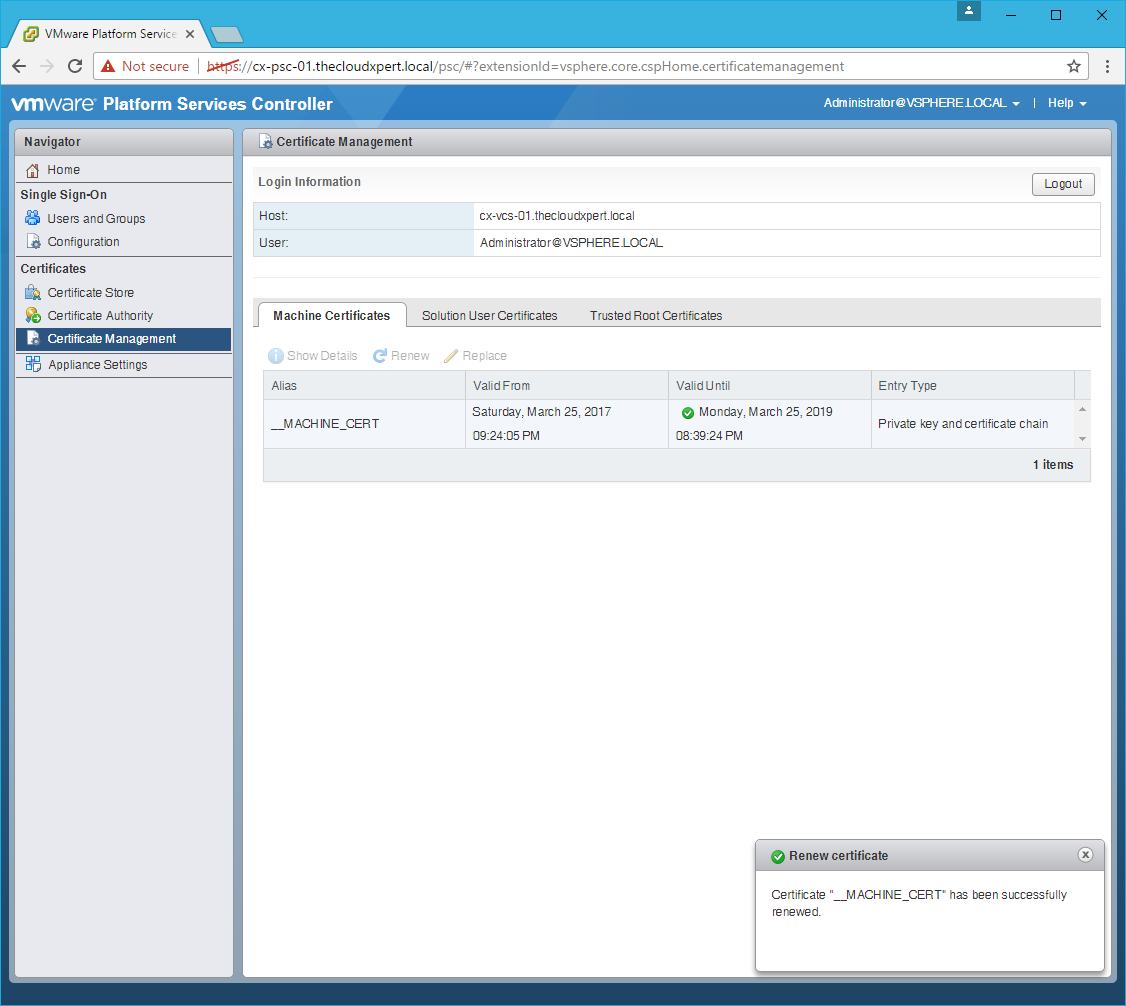
Renew the Solution User Certificates
- Click the Solution User Certificates tab.
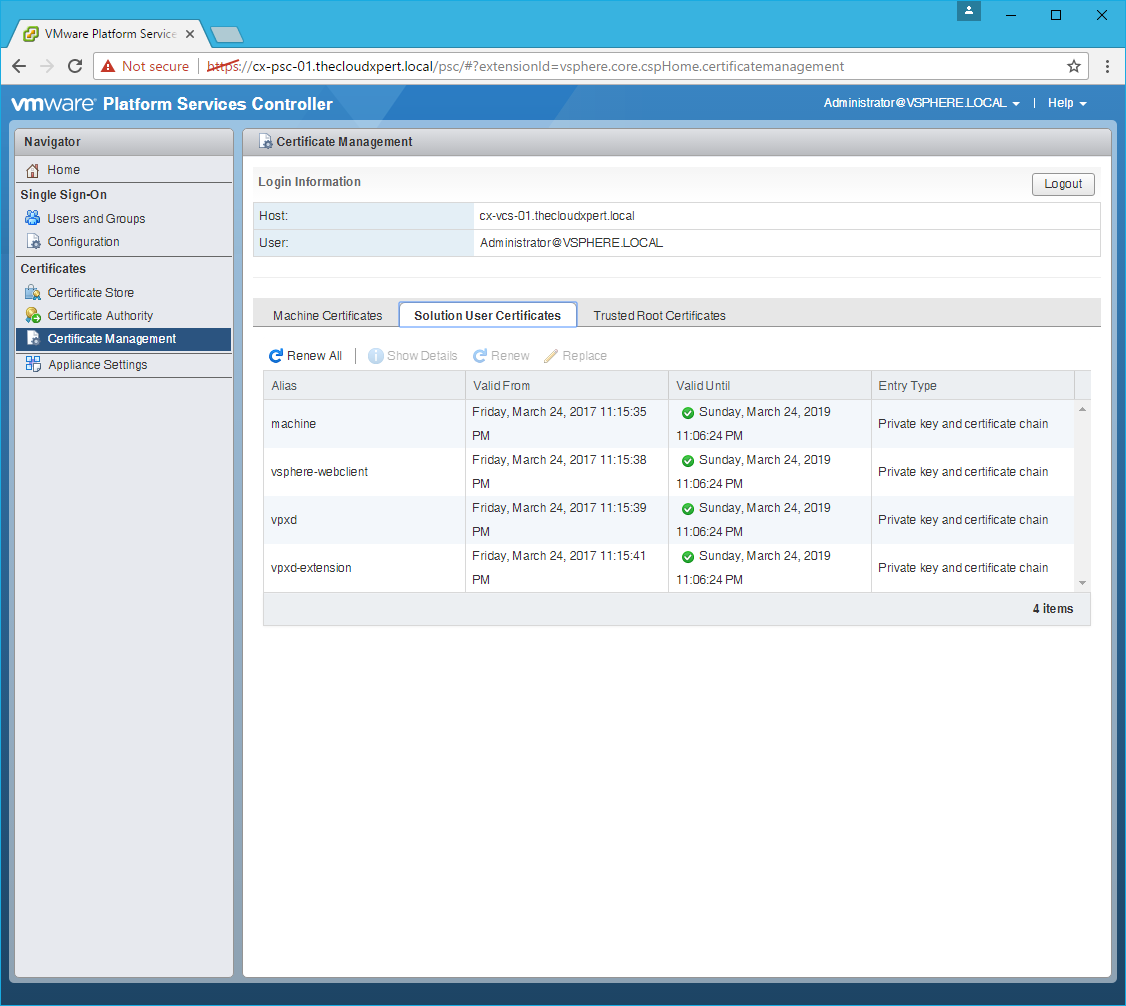
- Click Renew All.
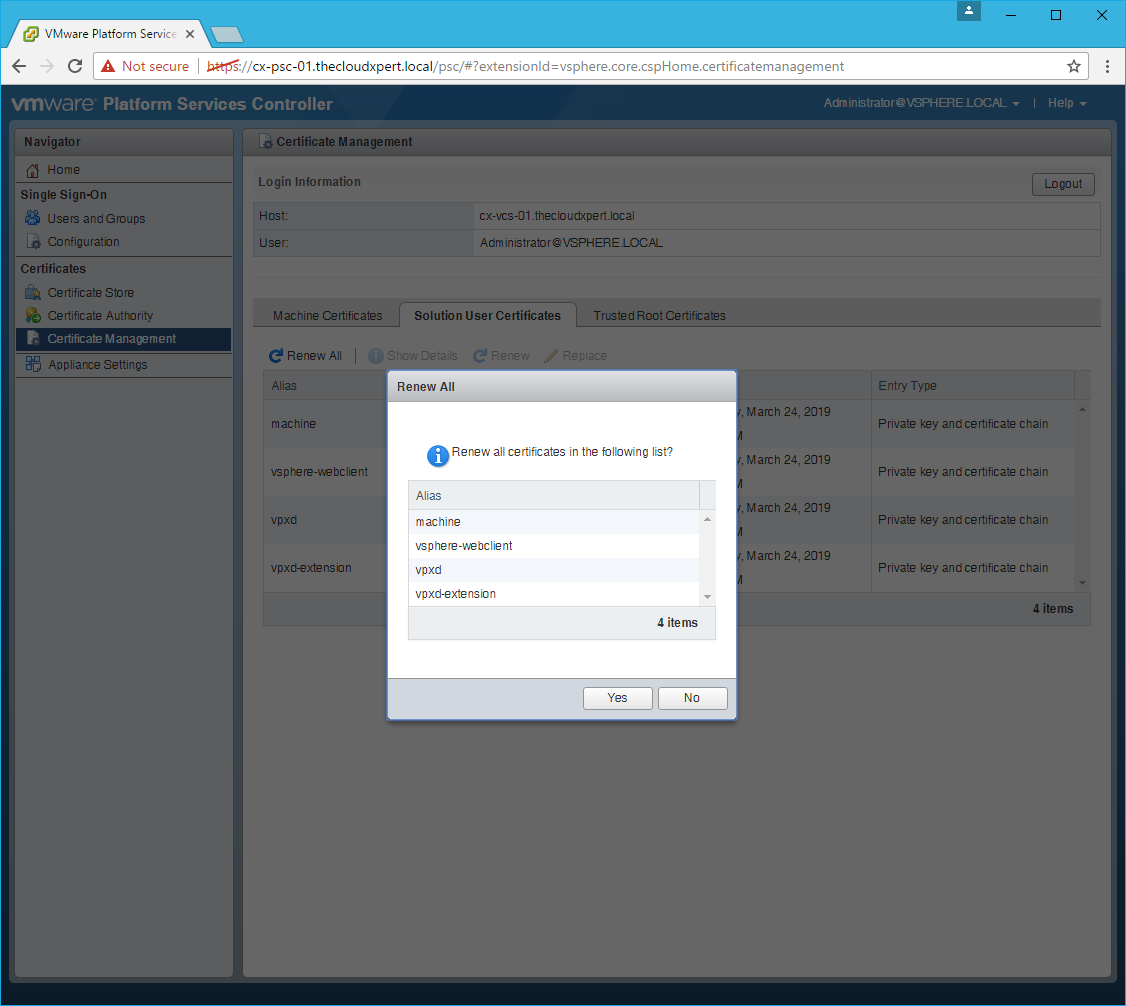
- Click Yes.
- Click Logout.
Reboot the Platform Services Controller
Note:
This can be completed in multiple ways but this is the way I did it.
- Click Appliance Settings.
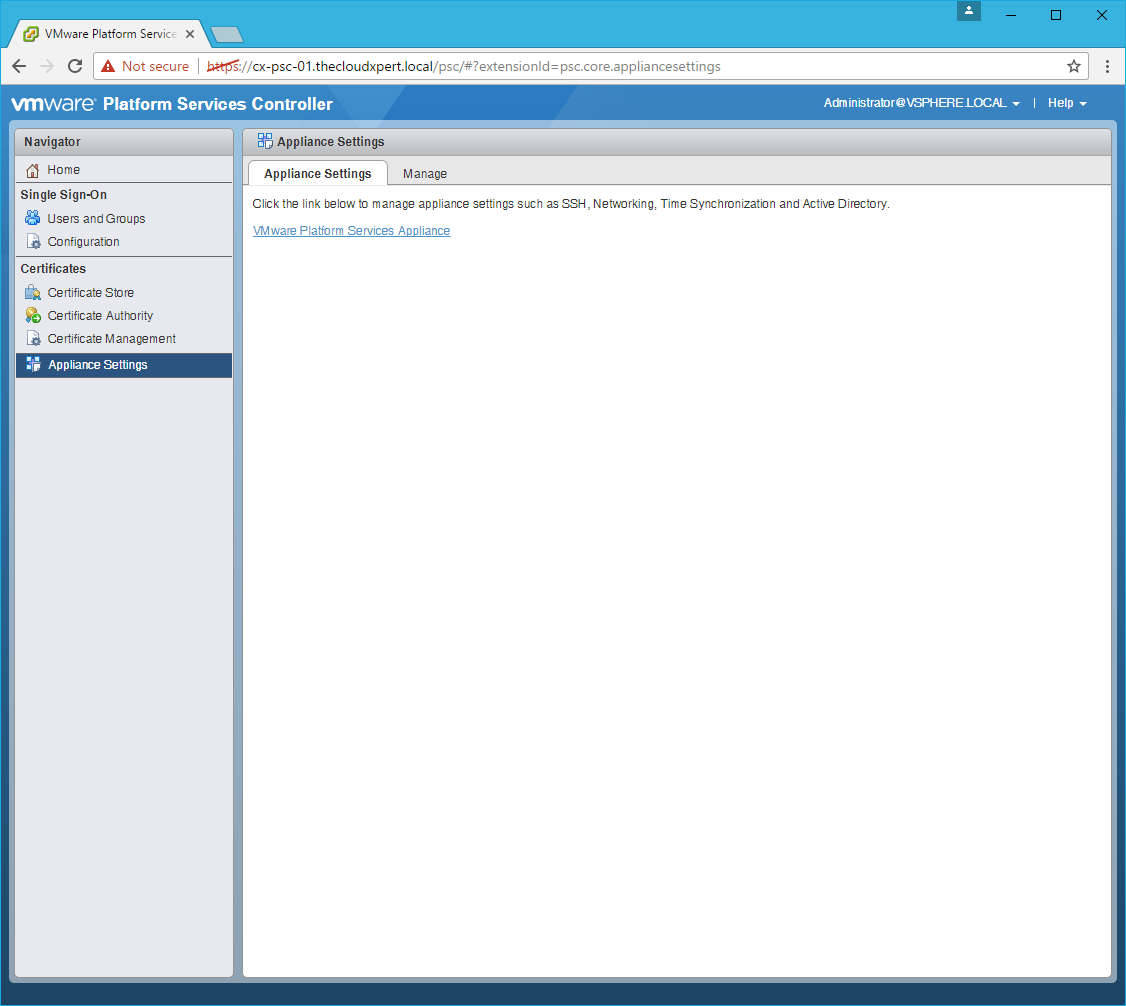
- Click the VMware Platform Services Appliance link.
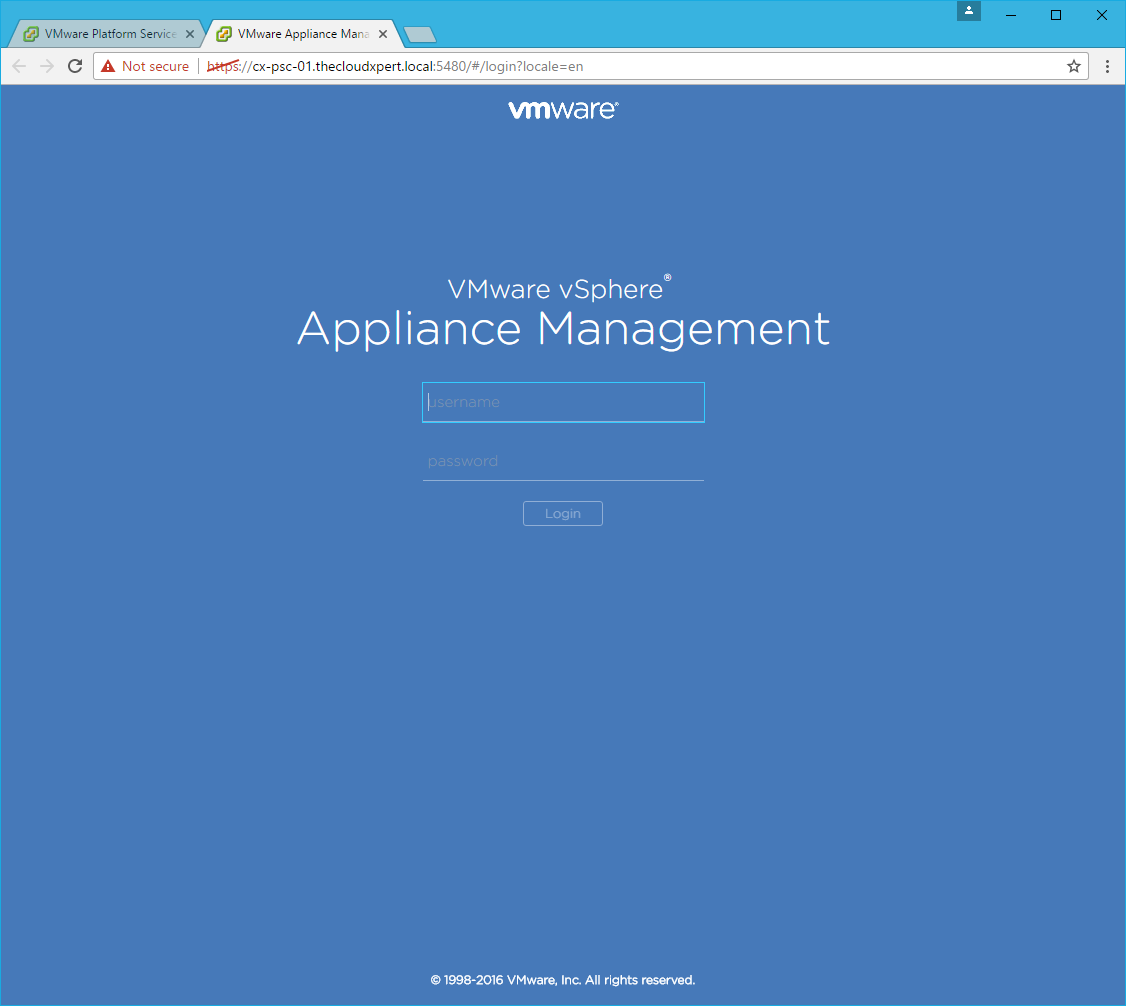
- Enter username as
rootand the root password, then click Logon.
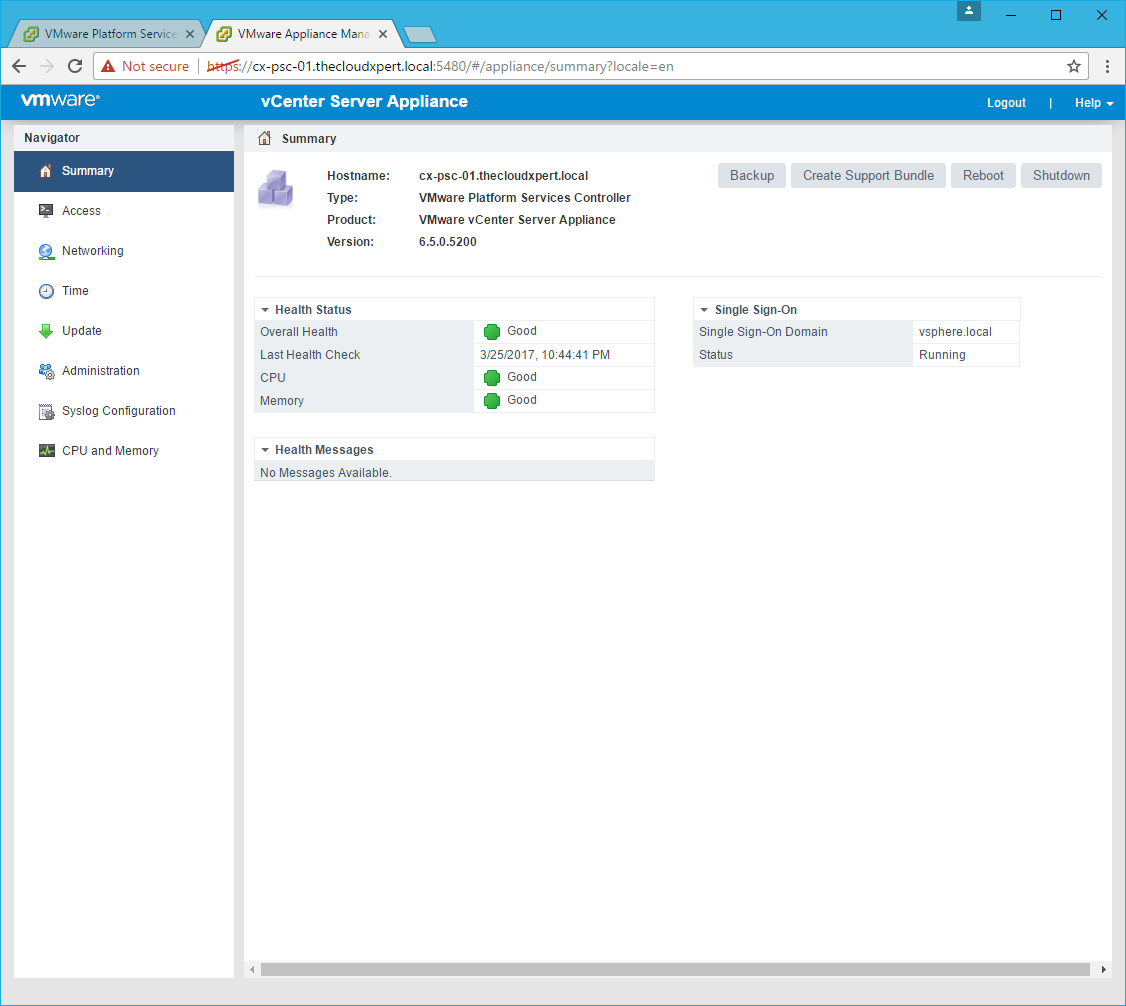
- Click Reboot.
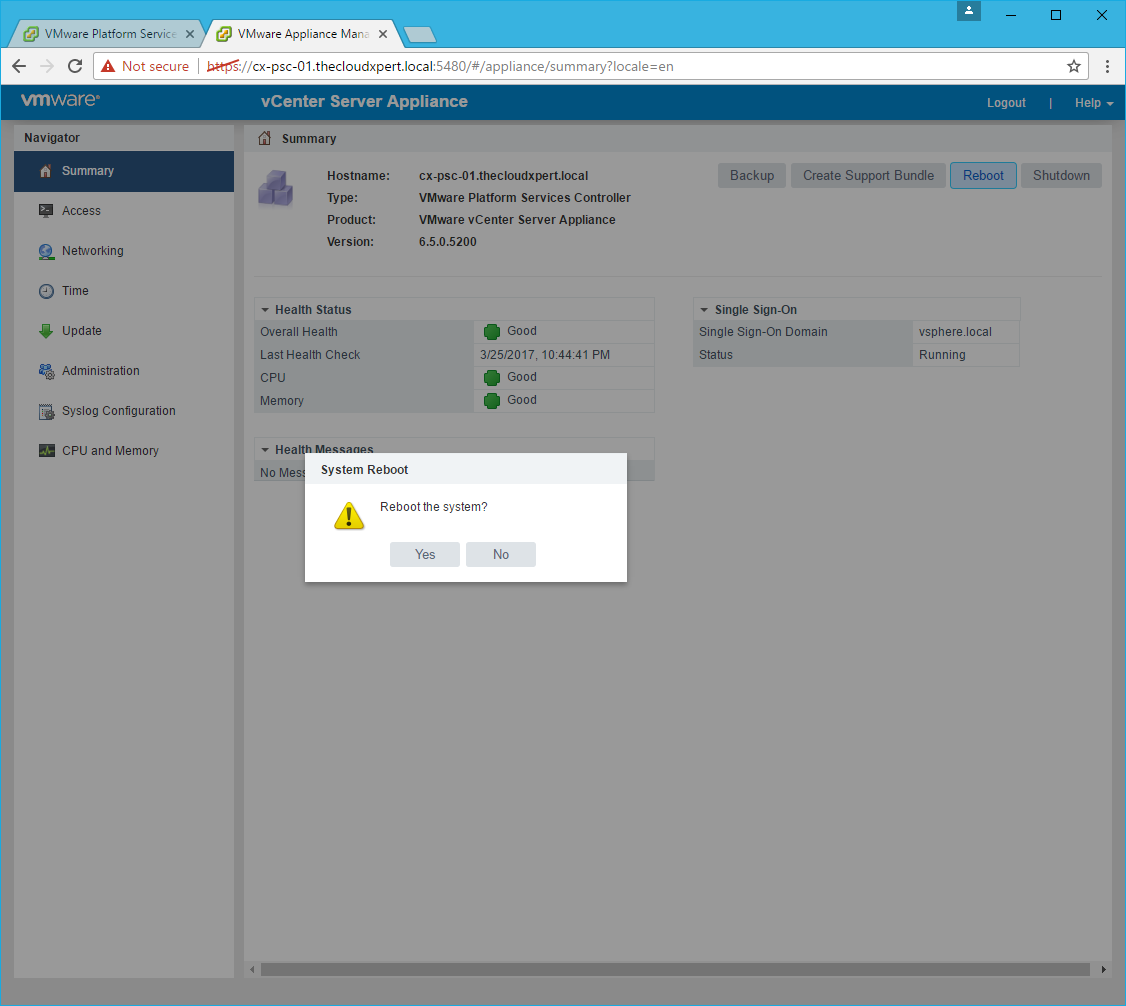
- Click Yes.
There we have it, your VCSA should now be acting as a Subordinate CA using the VMCA solution!
Published on 25 March 2017 by Christopher Lewis. Words: 344. Reading Time: 2 mins.
Related Post(s):
- HOWTO: Deploy a vSphere 6.5 vCenter Server Appliance (VCSA) ()
- HOWTO: Deploy a vSphere 6.5 External Platform Services Controller (VCSA) ()
- HOWTO: Automate the installation of the External Platform Services Controller using PowerCLI & JSON - Part 2 ()
- HOWTO: Automate the installation of the External Platform Services Controller using PowerCLI & JSON - Part 1 ()
- HOWTO: Deploy the VMware vSphere 6.0 Platform Service Controller ()
Recent Posts:
Blog Categories:
active directory 6
aria automation 9
aria automation orchestrator 1
aria operations 2
aws 2
blog 1
career 1
certificate authority 5
certificates 5
certification 91
cloud management 1
cloudnativecon 1
community 1
fun 1
general 9
hands on labs 1
home lab 2
kubecon 1
kubernetes 1
microsoft 7
nsx 45
nsx v 41
powercli 8
powershell 6
reviews 1
vcap 48
vcap6 2
vcenter 4
vcix 2
vexpert 9
vmug 5
vmware 99+
vmware aria 1
vmware aria automation 9
vmware aria automation orchestrator 1
vmware aria operations 5
vmware cloud 3
vmware cloud director 1
vmware explore 2
vmware identity manager 2
vmworld 36
vrealize automation 80
vrealize automation saltstack config 1
vrealize business 2
vrealize log insight 1
vrealize operations 1
vrealize operations manager 5
vrealize orchestrator 13
vrealize suite 14
vrealize suite lifecycle manager 20
vsan 5
vsphere 9
windows 6
Top Tags:
active directory 6
api 18
barcelona 24
certificates 11
certification 7
howto 33
microsoft 7
multi tenancy 9
nsx v 43
platform services controller 8
powercli 8
powershell 7
psc 6
vcap 9
vcap6 45
vcap6 cma 48
vcap6 nv 37
vcix6 nv 36
vexpert 19
vmug 8
vmware 99+
vmware aria 12
vmware aria automation 9
vmworld 35
vmworld 2016 13
vmworld 2017 9
vra 13
vrealize automation 74
vrealize operations 8
vrealize orchestrator 21
vrealize suite lifecycle manager 11
vrslcm 20
vsan 7
vsphere 12
