VMworld 2017 - Day 1 - Session(s)
Barcelona Cloud NSX VMConAWS VMworld VMworld 2017
Published on 12 September 2017 by Christopher Lewis. Words: 862. Reading Time: 5 mins.
Introduction
Day 1 of VMworld 2017 in Barcelona kicked off with another General Session .
Session Overviews
Following the General Session, I attended the following sessions:
Session 1 - #MMC1532BE - Using VMware NSX Cloud for Enhanced Networking and Security for AWS Native Cloud

With Amol Tipnis and Percy Wadia
This session concentrated on how VMware NSX Cloud can be used to provide a single pane of glass across multiple public clouds. Note: Currently VMware NSX Cloud is only available in AWS but development for MS Azure is on going.
The session started by highlighting the key challenges in Public Clouds covering the issues with Public Cloud lock-in, lack of visibility in and across the public cloud, and security and compliance across clouds. Enter VMware NSX Cloud to help address all of those issues that come with both single and multiple public clouds.
DEMO: Visibility through VMware NSX Cloud Manager
In this demo, Amol walked through the HTML5 interface covering multiple Amazon Virtual Private Cloud (VPC)s.
- Single Pane of Glass across all VPCs and all accounts and all clouds.
- A Single Security Posture Across your Hybrid Cloud
- Real Time Operational Visibility into Firewall Rule
- Defense in Depth through Default Quarantine
- Extend Enterprise Network Policy to Cloud
- Network Trace and Visibility
DEMO: Decoupling Application Deployment and Security
This pre-recorded demo covered the firewall configuration and dynamic group memberships across VPCs.
DEMO: Multi-layered Security through Default Quarantine
This demo showed a brief look at how VMware NSX Cloud can use default rules to ensure unmanaged VMs are immediately quarantined.
DEMO: Troubleshooting through NSX Traceflow
This demo showed using VMware NSX Traceflow in VMware NSX Cloud which showed a very cool network map of the flow in the HTML5 client.
Key takeaways:
- There is (almost) feature parity between VMware NSX Cloud and VMware NSX.
- A Dedicated instance for you Cloud environment - no sharing of data/networks.
- A VMware NSX Gateway is required per VPC.
- Infrastructure managed by VMware with no visibility into customer networks (unless granted).
For more information, see the session playback here .
Session 2 - #LHC3376BES - AWS Native Services Integration with VMware Cloud on AWS

The session is looking at how customers on VMware Cloud on AWS can integrate with the native AWS services create a hybrid cloud that best leverages the best of both VMware and AWS over low latency links between the two VPCs.
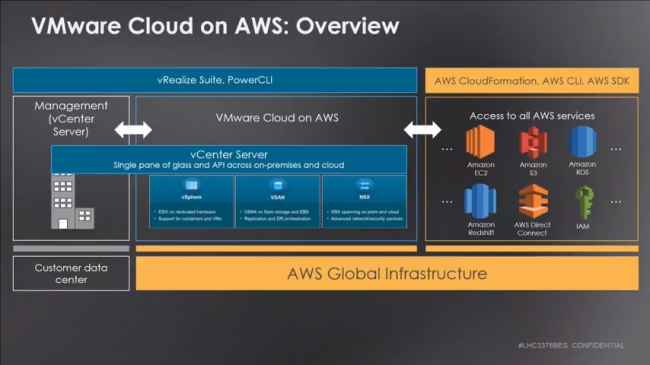
The session started with a brief overview of the architecture of VMware Cloud on AWS, for me the key takeaway here were:
- When transferring data between your AWS VPC and the VMConAWS managed VPC, there are no egress charges as it is classed as internal traffic which is low latency and high bandwidth.
- Initial deployment takes ~2 hours (4 hosts) and about 15 minutes per host after this.
- Based on AWS Hardware and not nested virtualisation.
Finally, Ian and Paul went through a few main use cases and how integration of native AWS services will provide a total solution for your VMware SDDC.
For more information, see the session playback here .
Session 3 - #LHC3375BES - VMware Cloud on AWS Hybrid Cloud Architectural Deep Dive: Networking and Storage Best Practices

Within this session, Aarthi and Wen covered the VMConAWS onboarding experience, the connectivity options and then covered both networking and storage best practices. This was a very comprehensive session around storage and networking capabilities.
Key Takeaways
- Hybrid cloud, there are Two AWS accounts:
- The VMware Cloud on AWS SDDC Account - owned and controlled by VMware.
- The Customer AWS account - owned and controlled by the Customer.
- Connectivity between the two accounts is via an Elastic Network Interface (ENI).
- Simple 4 Step onboarding process:
- Connect Customer AWS Account to the VMware Cloud AWS SDDC Account.
- Define SDDC Properties (the name of the SDDC, number of hosts and the region)
- Select VPC and subnets to use in the Customer AWS account
- Configure Management Network
- Within the Customer AWS account, A “cross-account” role is created and VMware are granted access to it - can be deleted at anytime and can be audited by AWS CloudTrail.
- Initial VMConAWS deployment takes < 2 hours.
- Best Practice is to connect L3 IPSec VPN to the Management and Compute Gateways.
- AWS Direct Connect connectivity to VMConAWS is roadmap.
- Internet connectivity from the VMConAWS instance is via the AWS Internet Gateway (IGW)
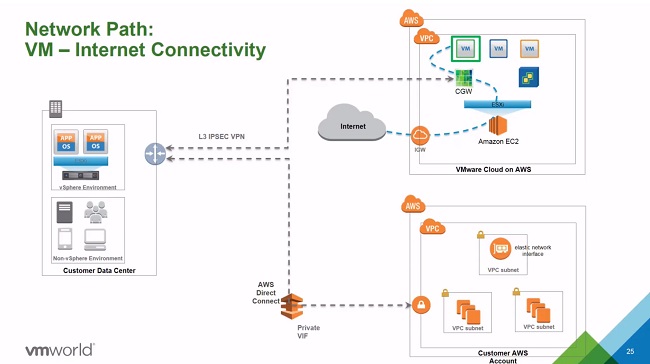
- The ENI is an interface on each VMConAWS ESX host that allows connectivity to the Customer VPC.
- Connectivity to Amazon S3 is now via the VPC and a Storage Gateway
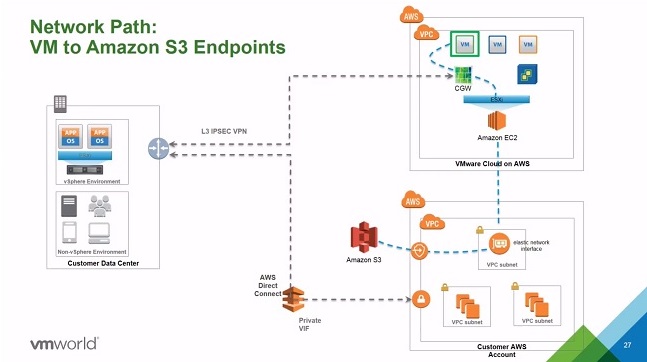
Wen Yu then took to the floor to discus the storage architecture.
- The AWS Integrated Storage Services available:
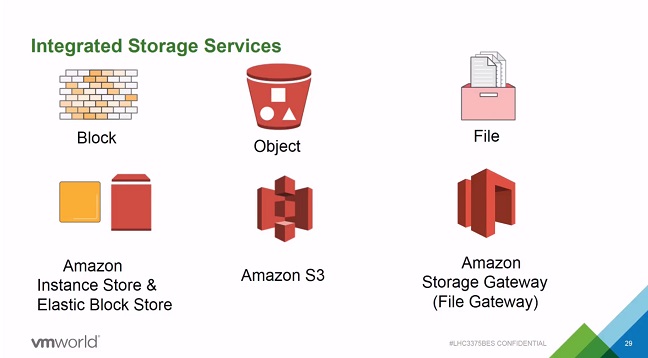
- The AWS Instance Store is used for primary storage. Based on NVMe Flash, Encrypted at Rest. Known as ephemeral storage so there is no replication of data blocks. However VMware VSAN will be responsible for this.
- The Amazon Elastic Block Store serves the boot media for VMware ESXi.
Wen Yu went on to discuss use cases for File Services, Backup to the cloud (using native Cloud Connectors (using Commvault or Veritas NetBackup) and Amazon Storage Gateways) , Data Protection and VM Restore.
For more information, see the session playback here .
Published on 12 September 2017 by Christopher Lewis. Words: 862. Reading Time: 5 mins.
