Replacing the vRealize Automation 7.3 Appliance Certificate
Certificates VMware vRealize Automation vRealize Orchestrator
Published on 11 December 2017 by Christopher Lewis. Words: 471. Reading Time: 3 mins.
Introduction
This is the first in a series of posts covering the replacement of vRealize Automation SSL Certificates.
For the purpose of these posts, I have deployed vRealize Automation 7.3 environment with self signed certificates. This means that when you navigate to https://vra7.fqdn/vcac, the site is not secure nor trusted. Therefore, you will be presented with something like the following in your browser (I mostly use Chrome):

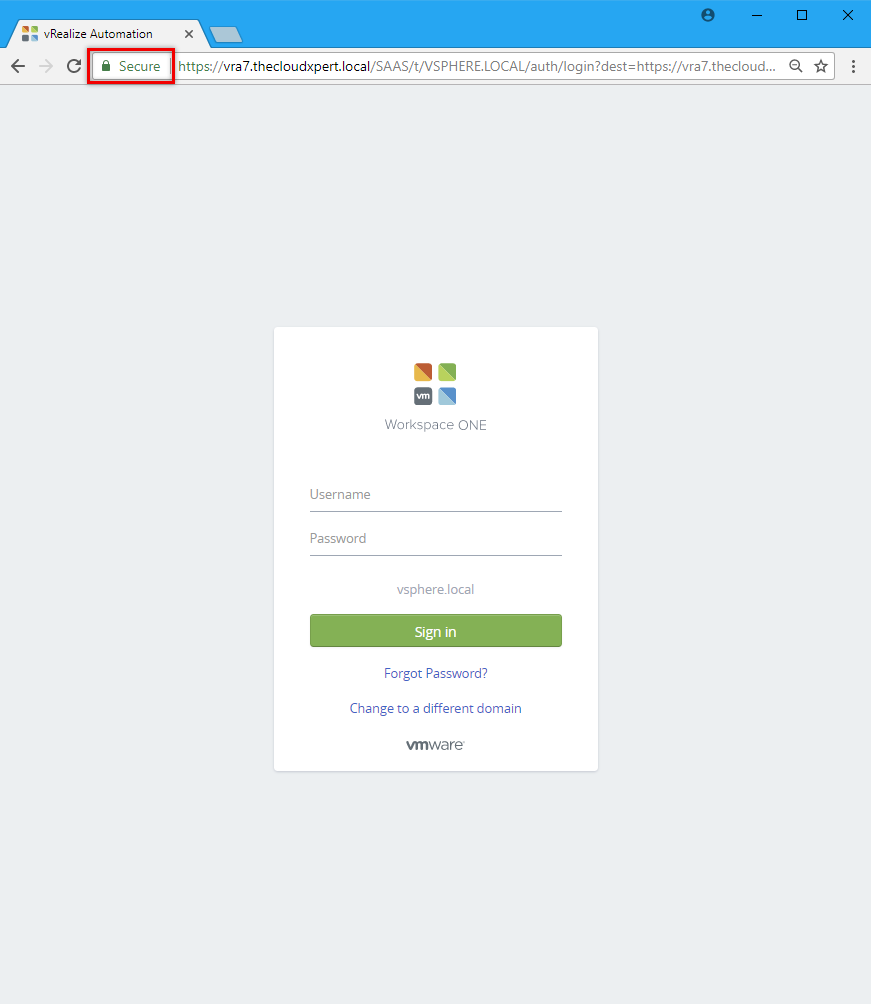
We’re looking to achieve the following in the browser URL bar after the certificate has been replaced.

or
This post is based on the VMware procedure and this is documented here .
Step By Step Guide
Prerequisites
The following are expected prerequisites for this walkthrough:
- A fully deployed and working vRealize Automation solution.
- A set of certificate files:
- The RSA Private Key used to encrypt the vRA certificate.
- The Root CA Certificate file.
- The vRA Certificate file.
- The Root CA Certificate and any Subordinate/Intermediate CA Certificates are installed within the appropriate Certificate store on the local machine (normally the Trusted Root Certification Authorities and the Intermediate Certification Authority respectively).
Replacing the vRealize Automation Appliance Certificate
- Navigate to the vRealize Automation Appliances Virtual Appliance Management Infrastructure (VAMI) interface,
https://vra.fqdn:5480.
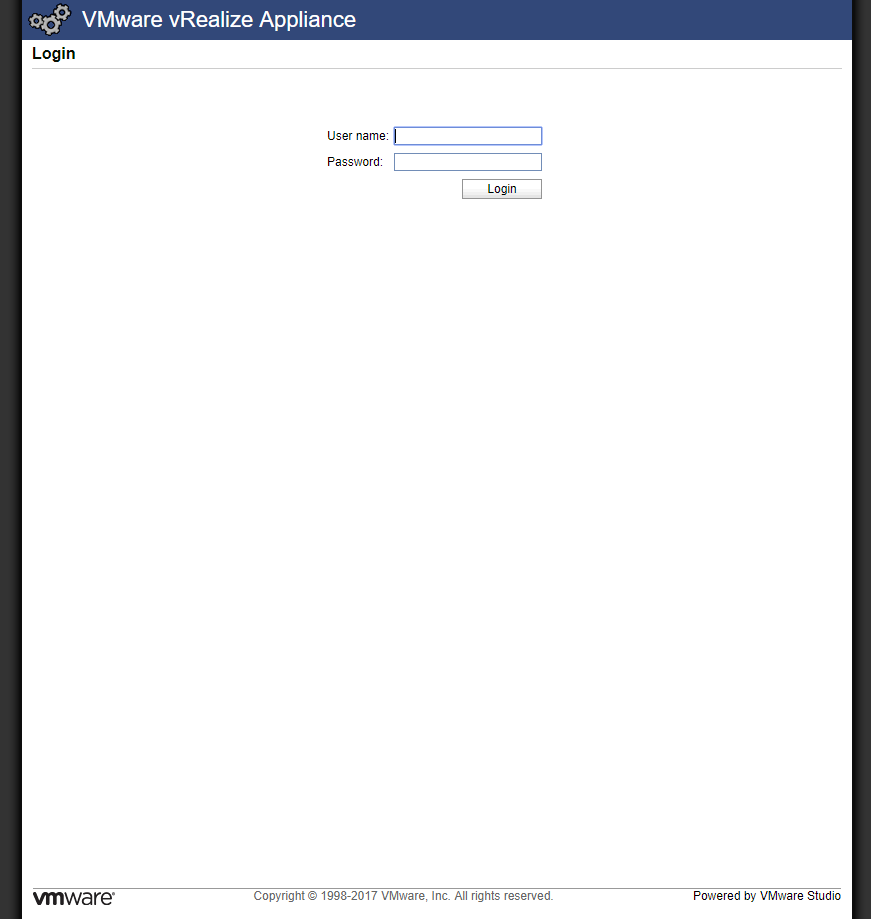
- Log into the VAMI by typing the User Name and Password configured during the install wizard and clicking Login.
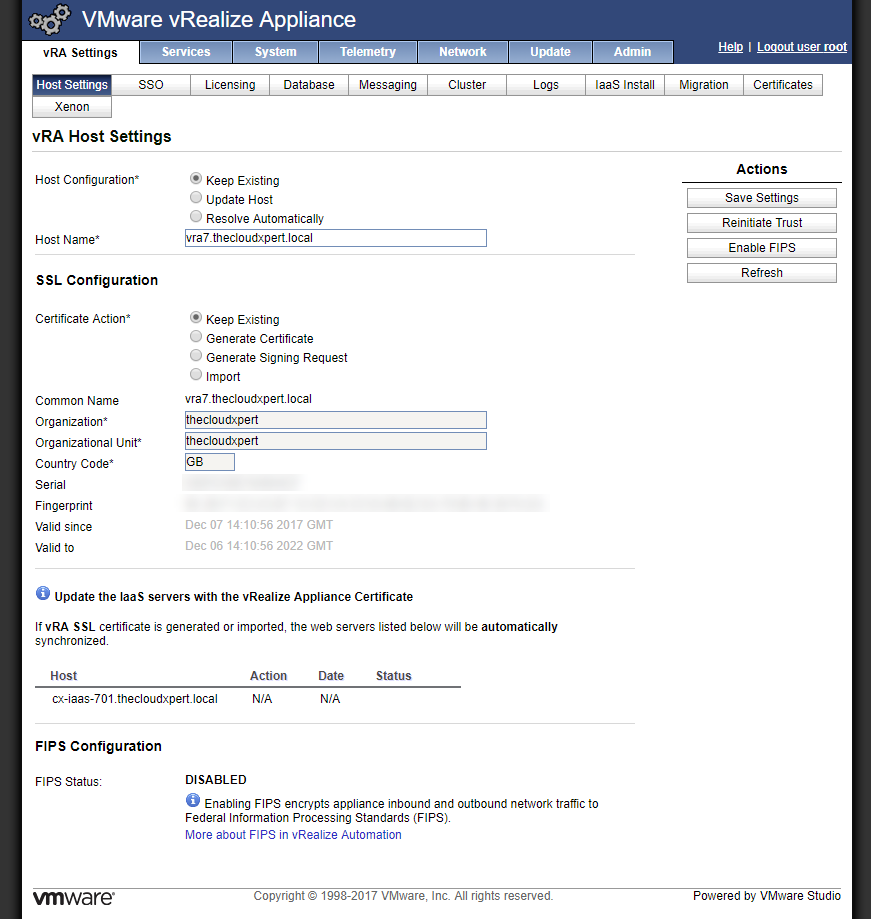
- Under SSL Configuration, select the Import option.
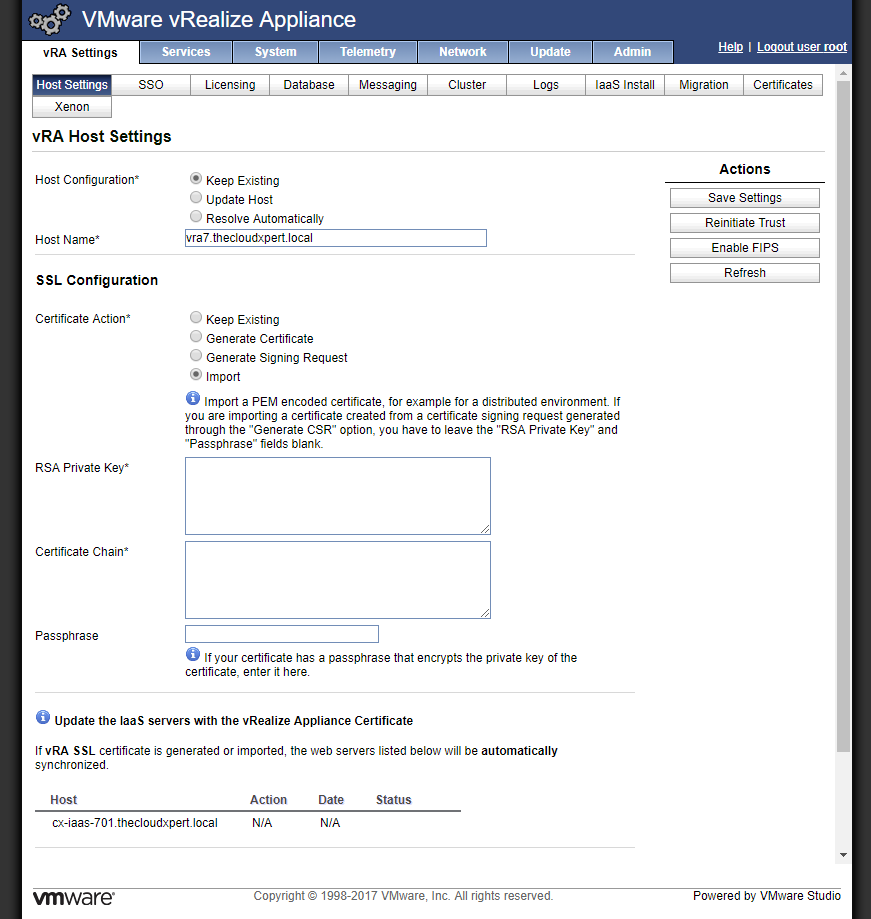
- Open the RSA Private Key file in a text editor and copy and paste the information into the RSA Private Key field.
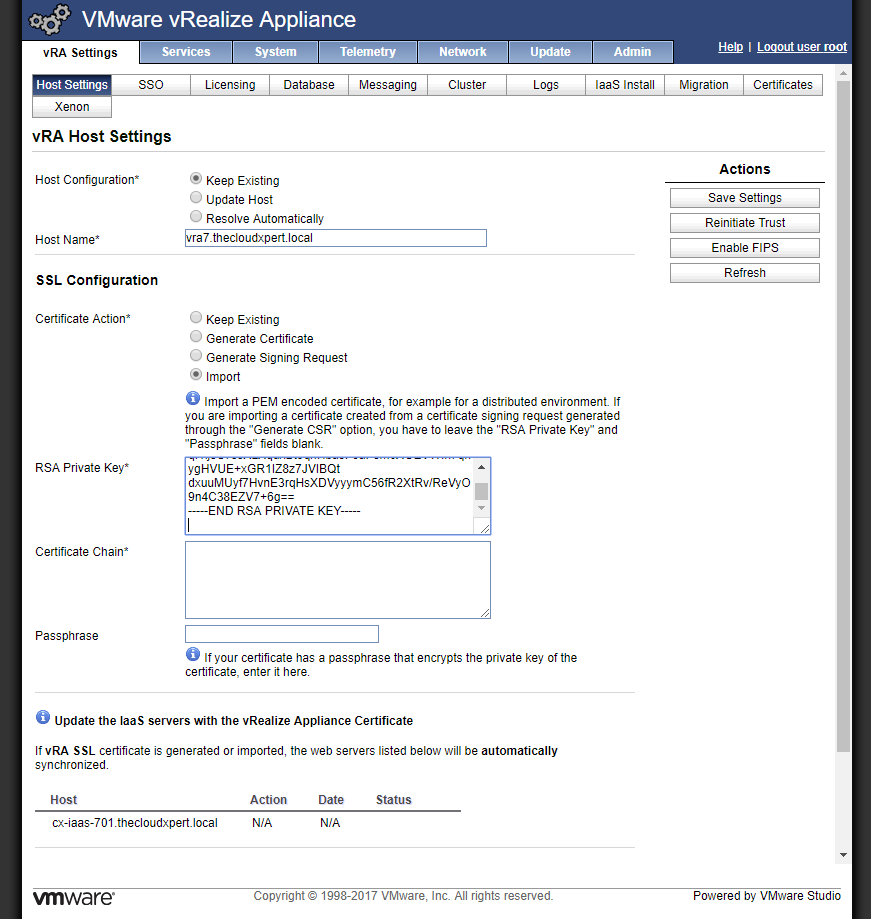
-----BEGIN RSA PRIVATE KEY----- and -----END RSA PRIVATE KEY----- text.
- Open the Certificate, Intermediate CA (if applicable) and the Root Certificate file(s) in a text editor and copy and paste the information into the Certificate Chain text field.
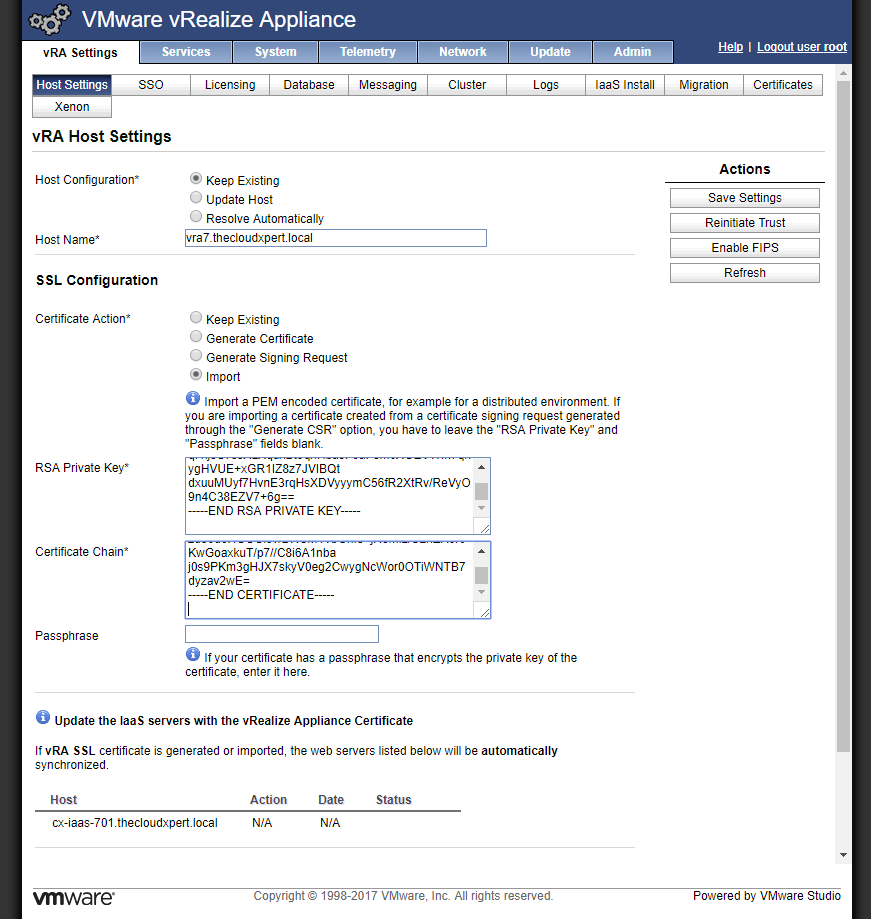
- You should include the
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----text for each certificate. - The client SSL certificate should be first, then any intermediate CA certificates, followed by the Root CA certificate.
-
If required, enter the Passphrase into the text field.
-
Under Actions, click Save Settings.
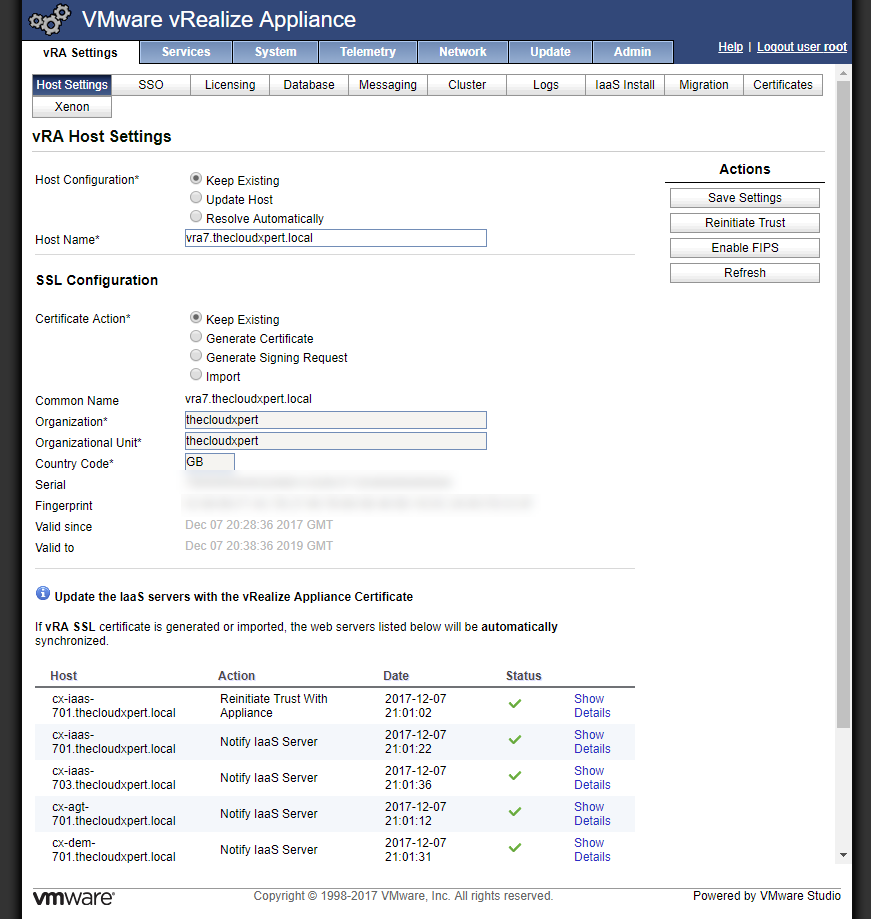
- Click Logout user root.
And there you have it!
Checking the certificate
When you now navigate to https://vra.fqdn/vcac you now get the green padlock to say the certificate is trusted and you immediately get a warm fuzzy feeling!
Next Step(s)
In the next post , we’ll look at Replacing the vRealize Automation 7.3 Infrastructure as a Service Web Certificate.
Published on 11 December 2017 by Christopher Lewis. Words: 471. Reading Time: 3 mins.
- Replacing SSL Certificates in vRealize Automation 7.3 ()
- vRealize Automation and Orchestrator 7.3 Released! ()
- HOWTO: Configure a vRealize Automation 6 Advanced Services Endpoint for vCenter Server ()
- VCAP6-CMA Deploy - Objective 6.1: Configure Advanced Service Designer ()
- HOWTO: Configure a vRealize Automation 6 Advanced Services Endpoint for Active Directory ()
